Simplified Firewall Management
Simplified Firewall Management
Simplified Firewall Management
Redesigning a centralized platform to monitor, manage and configure multiple firewalls globally.
Redesigning a centralized platform to monitor, manage and configure multiple firewalls globally.
Redesigning a centralized platform to monitor, manage and configure multiple firewalls globally.
My Role
My Role
Research and Analysis
Information Architecture
Task Flows
User Testing
Visual Design
Stakeholder and Project Management
Research and Analysis
Information Architecture
Task Flows
User Testing
Visual Design
Stakeholder and Project Management
Research and Analysis
Information Architecture
Task Flows
User Testing
Visual Design
Stakeholder and Project Management
Challenge
Challenge
---------------
---------------
In spite of being one of the leaders in the centralized firewall management system, their users ( Security Manager ) had a hard time monitoring, managing, and configuring multiple firewalls. Incoherence in the current system led users to distrust the capability of the product and depend on third-party applications.
In spite of being one of the leaders in the centralized firewall management system, their users had a hard time monitoring, managing and configuring multiple firewalls. Incoherence in the current system led users to distrust the capability of the product and depend on third-party applications.
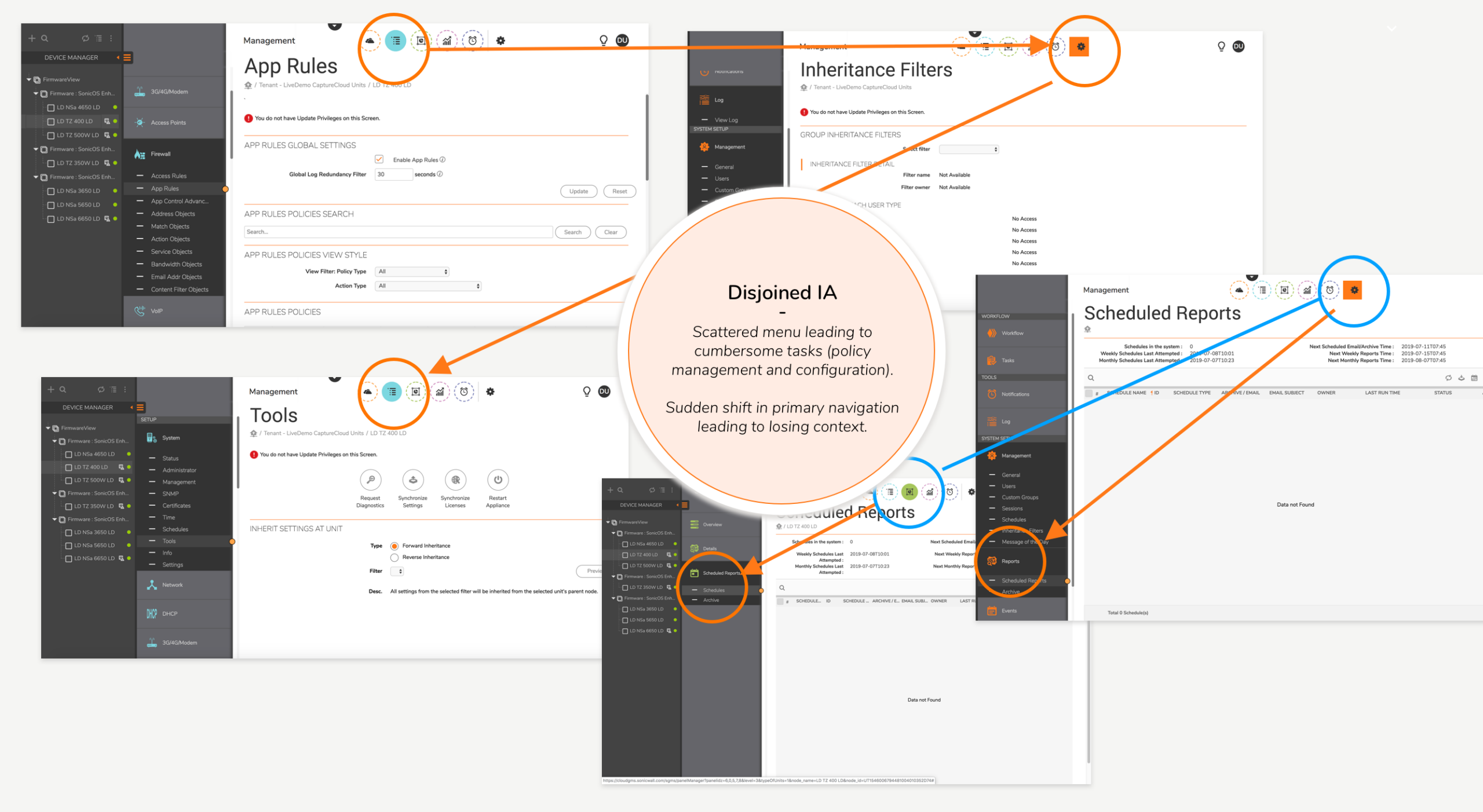
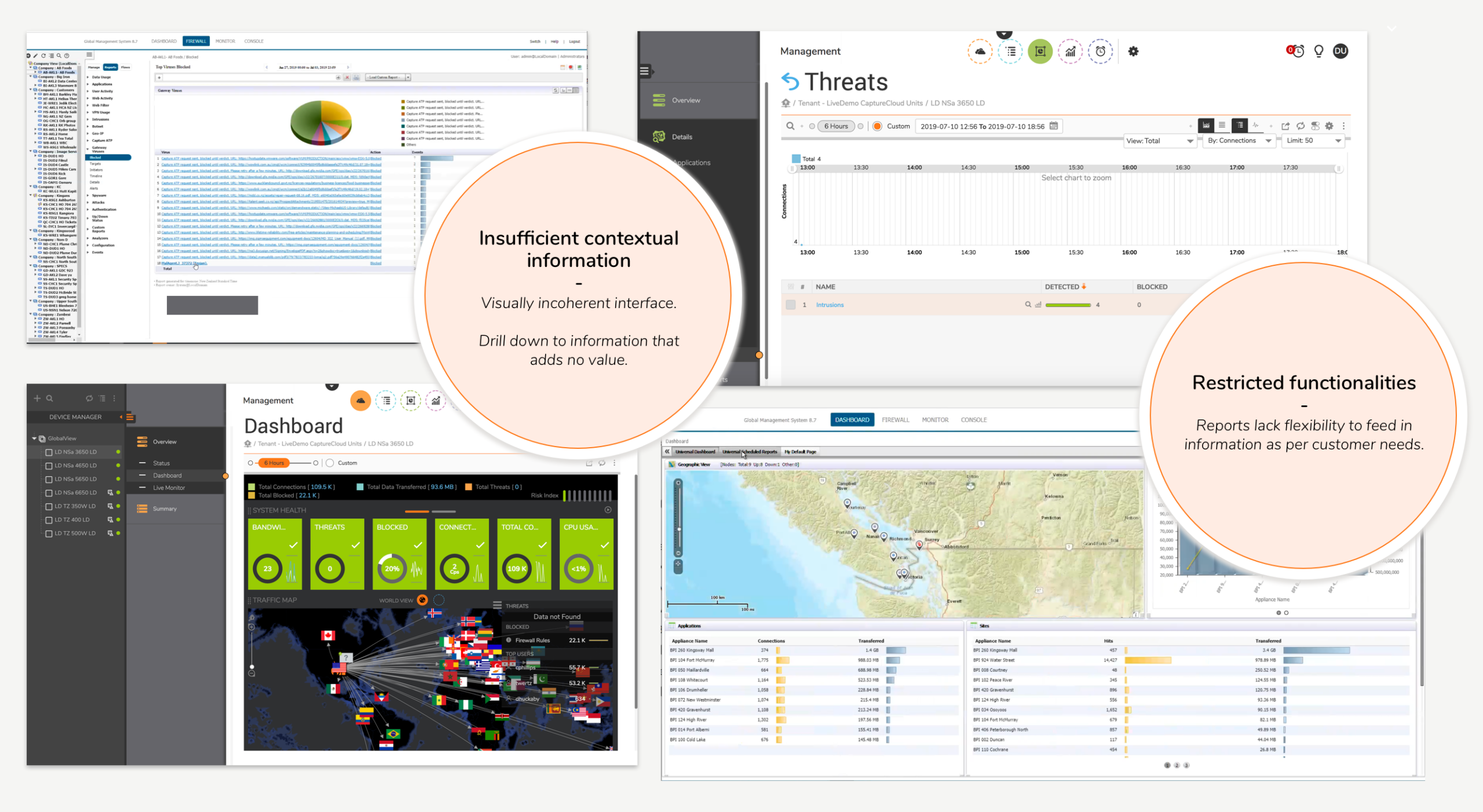
As a result, Security Engineer's day to day tasks became time-consuming and tedious.
Competitor products preferred over Firewall was a proven fact.
As a result, Security Engineer's day to day tasks became time-consuming and tedious.
Competitor products preferred over Firewall was a proven fact.
How might we help the Security Engineers efficiently trace anomalies, easily evaluate criticality and instantly take remedial actions?
How might we help the Security Engineers efficiently trace anomalies, easily evaluate criticality and instantly take remedial actions?
User Research & Insights
User Research & Insights
------------------------------------
---------------------------------
User Persona
User Persona

Qualitative Interview
Qualitative Interview
Interviewed 23 users across small, medium and large service providers and enterprise distributors. The research goal was to :
- Understand the nature and criticality of their tasks. What works, what doesn’t work and why?
- Get insights into user-specific needs and expectations from the application.
- Map frustrations and pain points around IA and specific task completion.
- Learn how well they understand the current interface (terminology and visual cues).
- Understanding their expectations and what they consider as best practices and why? (desires).
Interviewed 23 users across small, medium and large service providers and enterprise distributors. The research goal was to :
- Understand the nature and criticality of their tasks. What works, what doesn’t work and why?
- Get insights into user-specific needs and expectations from the application.
- Map frustrations and pain points around IA and specific task completion.
- Learn how well they understand the current interface (terminology and visual cues).
- Understanding their expectations and what they consider as best practices and why? (desires).
"Alerting is really bad in the application. The system does not tell us if the reports scheduled has failed to deliver. Hence someone has to check manually every week. We have to dig through emails and will be in trouble if we have not received one."
"Alerting is really bad in the application. The system does not tell us if the reports scheduled has failed to deliver. Hence someone has to check manually every week. We have to dig through emails and will be in trouble if we have not received one."
- Stephan Gladiadis, Boston Hut
- Stephan Gladiadis, Boston Hut

"A clears indication of where in the application or tree structure I am and how many firewalls are being affected is not provided when we push policies."
"A clears indication of where in the application or tree structure I am and how many firewalls are being affected is not provided when we push policies."
- Ron Culler, ADT
- Ron Culler, ADT

" It would be good to have default templates i.e, if one customer has 130 Firewalls, then we can have default configs ( templates ) for them and we just have to select and push these configs to the Firewalls."
" It would be good to have default templates i.e, if one customer has 130 Firewalls, then we can have default configs ( templates ) for them and we just have to select and push these configs to the Firewalls."
- Mike Newman, Westerns
- Mike Newman, Westerns

"Lack of business-specific reporting that is relevant to business owners - they want to know usage details about a specific employee. Their goal might be to see how productive their employees are."
"Lack of business-specific reporting that is relevant to business owners - they want to know usage details about a specific employee. Their goal might be to see how productive their employees are."
- Justin Penchina, Get Inc.
- Justin Penchina, Get Inc.
Most of the users said...
Most of the users said...
" I avoid using the current platform and continued to log-in to individual firewalls to push policies. "
"I avoid using the current platform and continued to log-in to individual firewalls to push policies."
" I have to constantly keep track of emails, individual dashboards, and ticketing systems for notifications. "
"I have to constantly keep track of emails, individual dashboards, and ticketing systems for notifications."
" I feel embarrassed when my customers track the anomalies and question my capability."
"I feel embarrassed when my customers track the anomalies and question my capability."
Journey Map
Journey Map
We created a journey map to understand the user's mental model in terms of emotions, feeling, and expectations at each task level. This helped us identify design opportunities.
We created a journey map to understand the user's mental model in terms of emotions, feeling, and expectations at each task level. This helped us identify design opportunities.
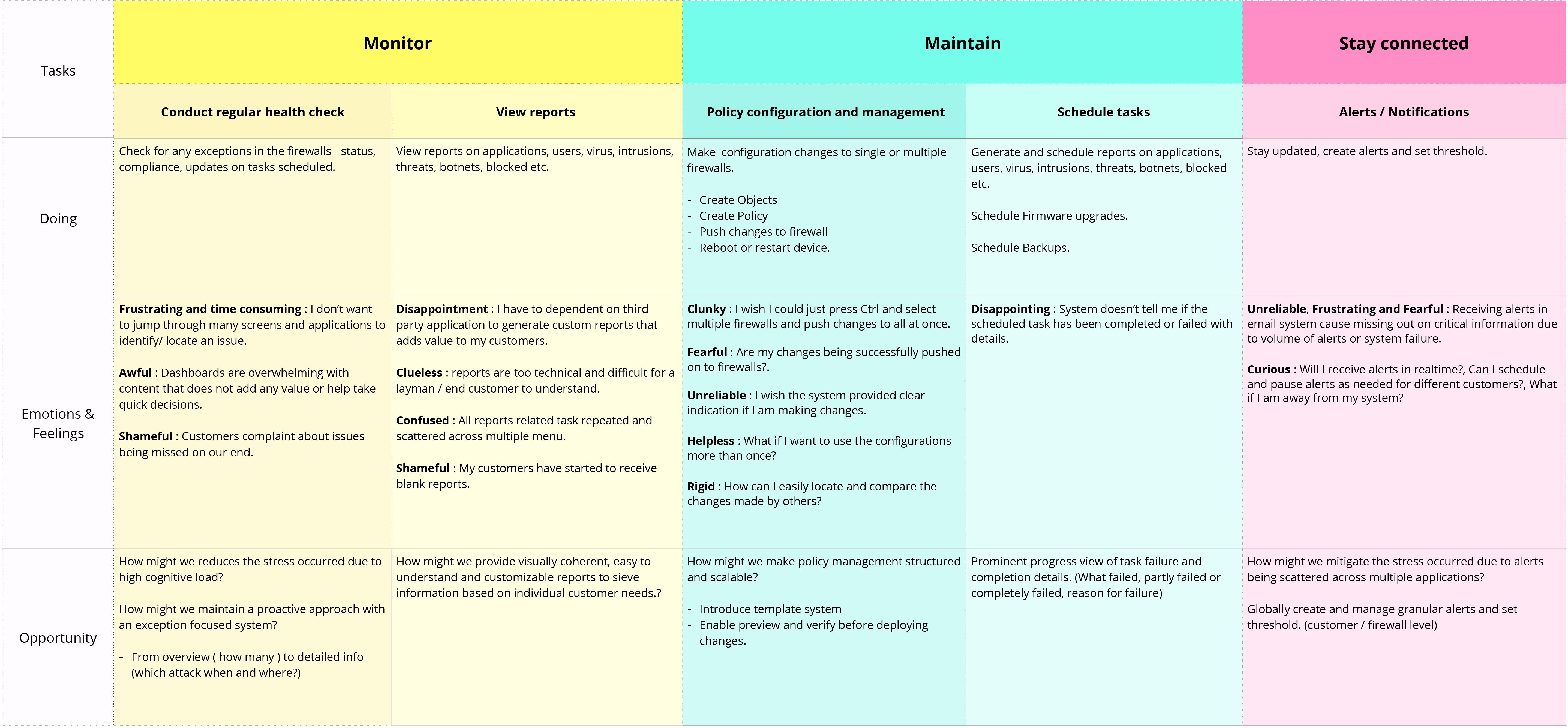
I also did a quick study on what it is like to design for the security domain. With constantly changing customer needs, new and emerging attacks every day, and small mistakes leading to larger impact: 1. Time is the key 2. Proactive approach over, reactive 3. Need to reduce cognitive load, Increase visibility, and be in total control.
Insights identified to efficiently trace anomalies
Insights




Design Direction / Solution
Design Direction
------------------------------------
----------------------------
I saw the need to look at the problem from a systemic aspect and redesigned application and the interrelationship between the functionalities based on well-defined design goals.
We saw the need to look at the problem from a systemic aspect and redesigned application and the interrelation of functionalities based on well-defined design goals.
A guided user interface with a clear and consistent navigational mechanism.
A guided user interface with Clear and Consistent navigational mechanisms.
Exception focused and justification driven task flows to mitigate risk.
Exception focused and justification driven task flows to mitigate risk.
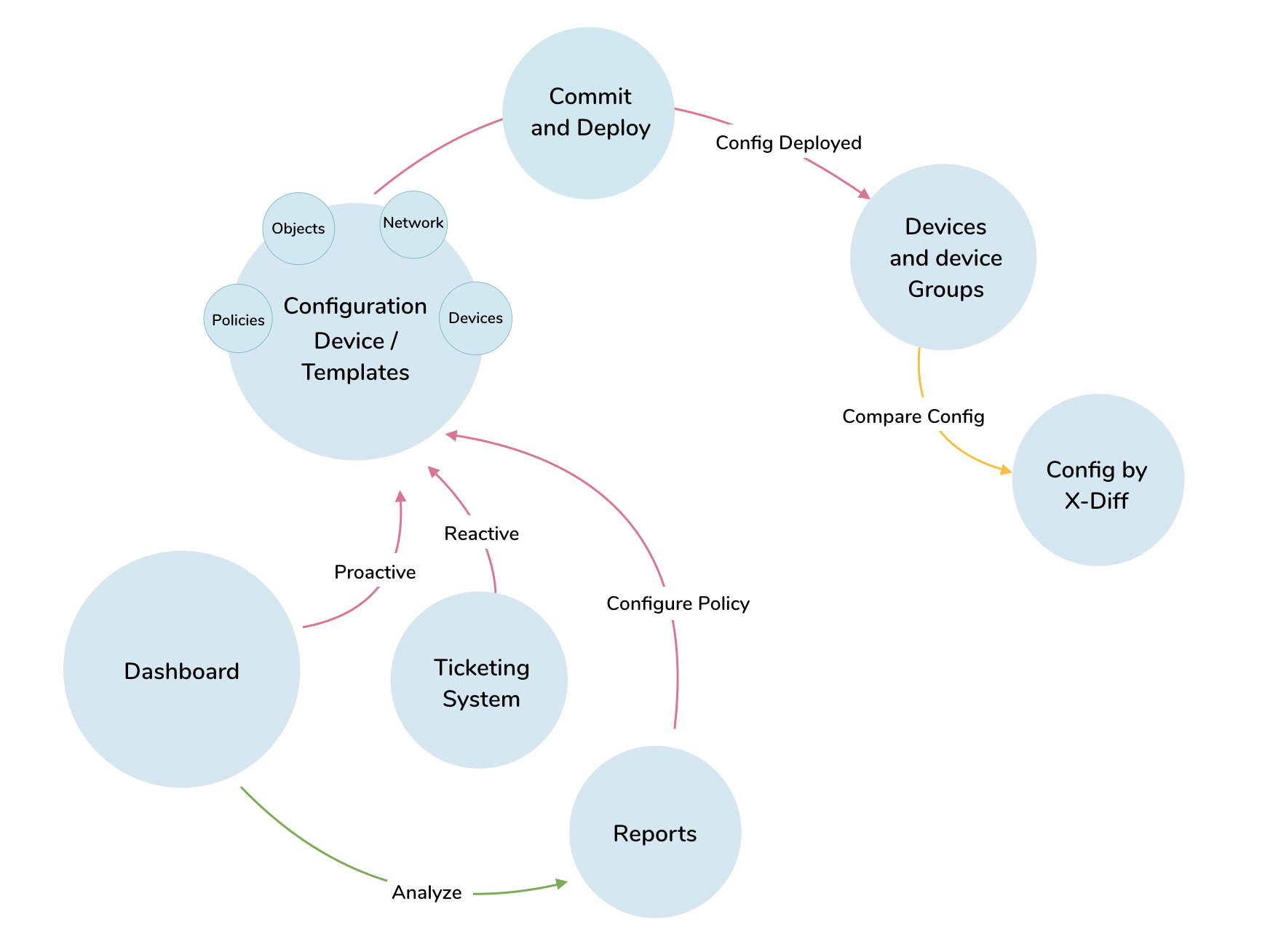
From Entity Relationship diagram to Information Architecture
Entity Relationship Diagram
Putting together an entity-relationship map helped us to define different entities within the system and how they need to connect with each other.
This helped us to better redefine the IA by grouping primary, secondary and tertiary level information with access only to what is relevant. Thus reducing cognitive load, helps stay focused and complete the task faster.
Putting together an entity-relationship map helped us to define different entities within the system and how they need to connect with each other.
This helped us to better redefine the IA by grouping primary, secondary and tertiary level information with access only to what is relevant. Thus reducing cognitive load, helps stay focused and complete the task faster.
A sneak peek into user scenarios and task flow development process
A sneak peek into user scenarios and task flow development process
Multiple user scenarios were put together and task flows were developed for each. This was run by product managers at different stages to ensuring that everyone is on the same page.
Multiple user scenarios were put together and task flows were developed for each which helped us to validate the design with users and stakeholders at different stages of the project. This also helped us to ensure that everyone is on the same page.
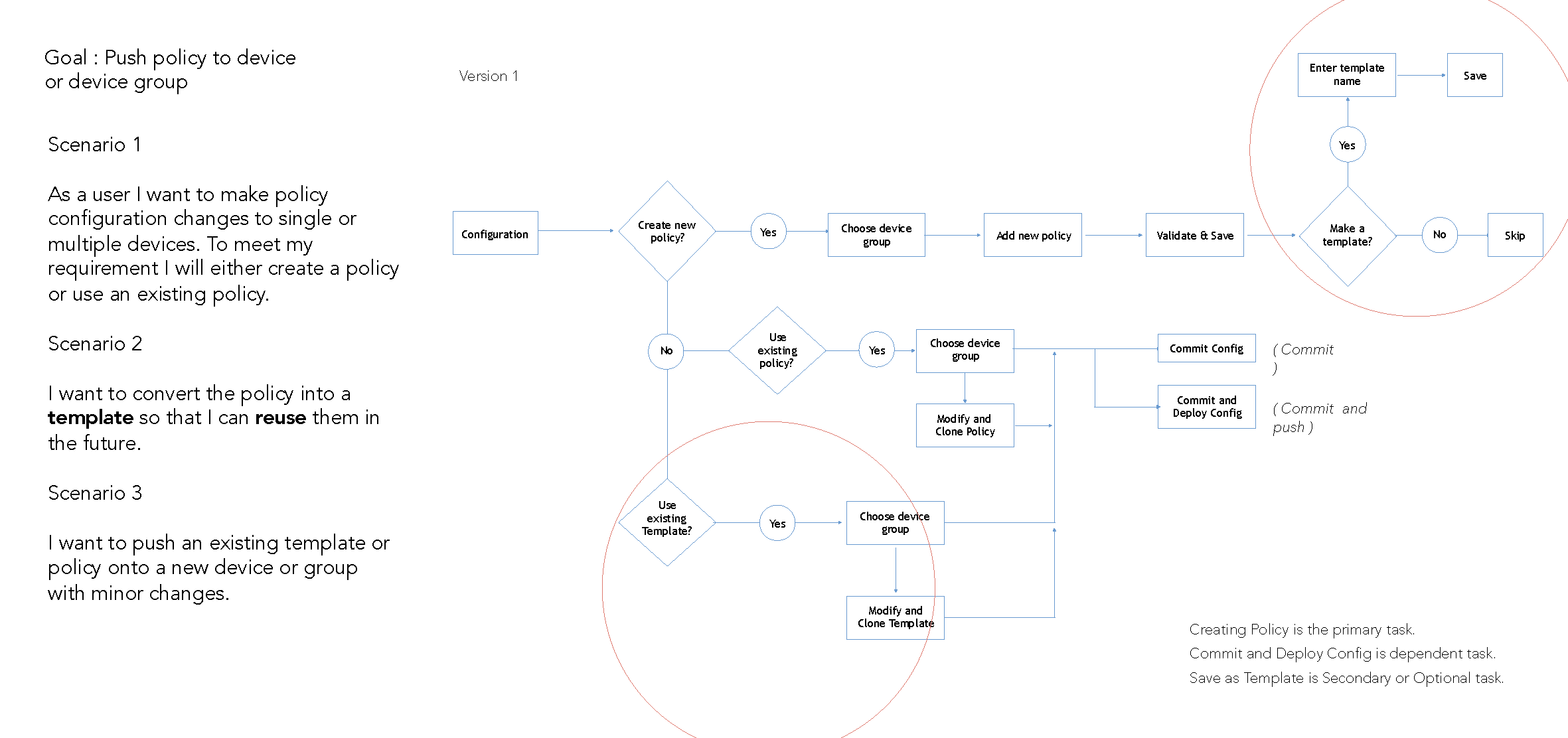
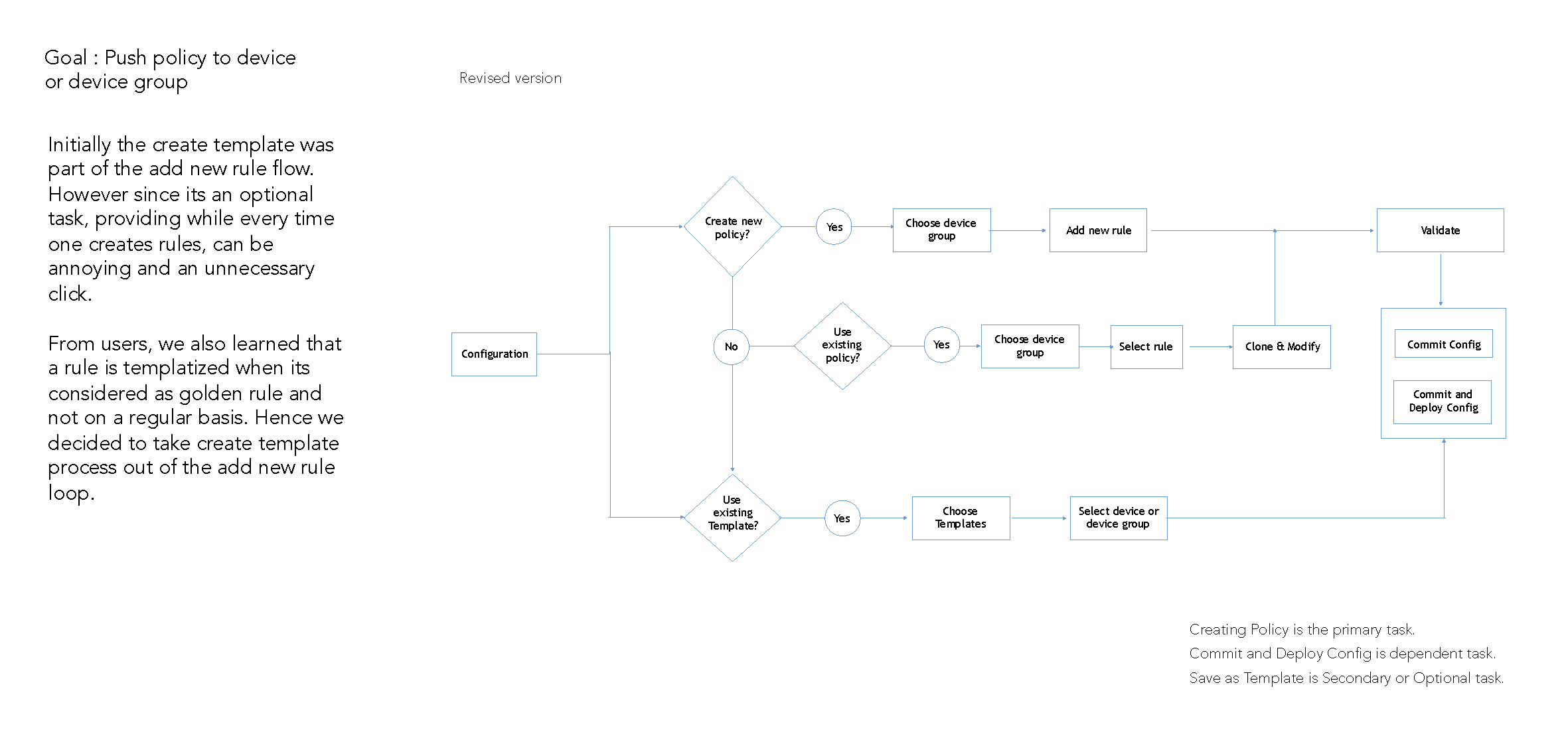
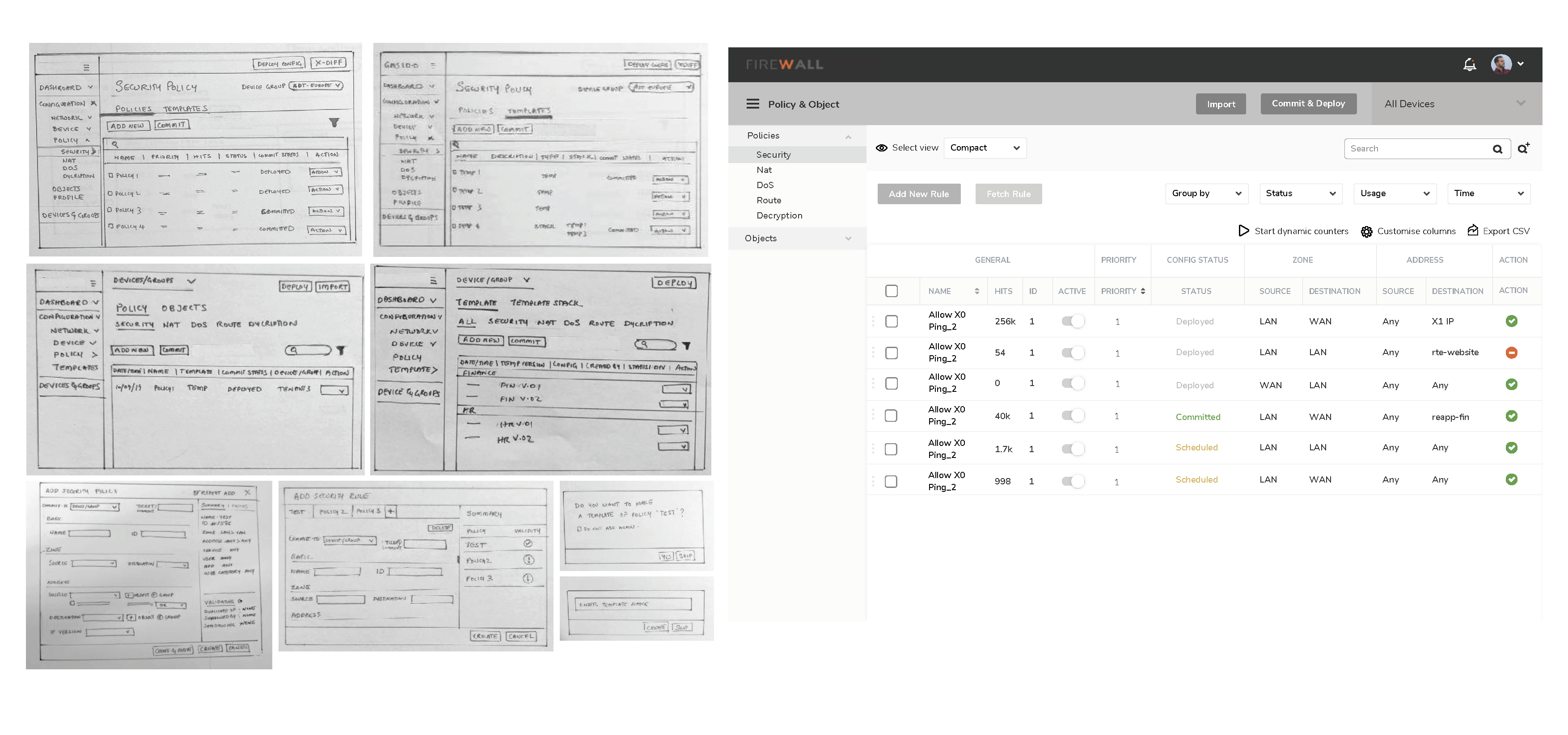
Application features and its functionalities redefined
Application features and its functionalities redefined
--------------------------------
--------------------------------
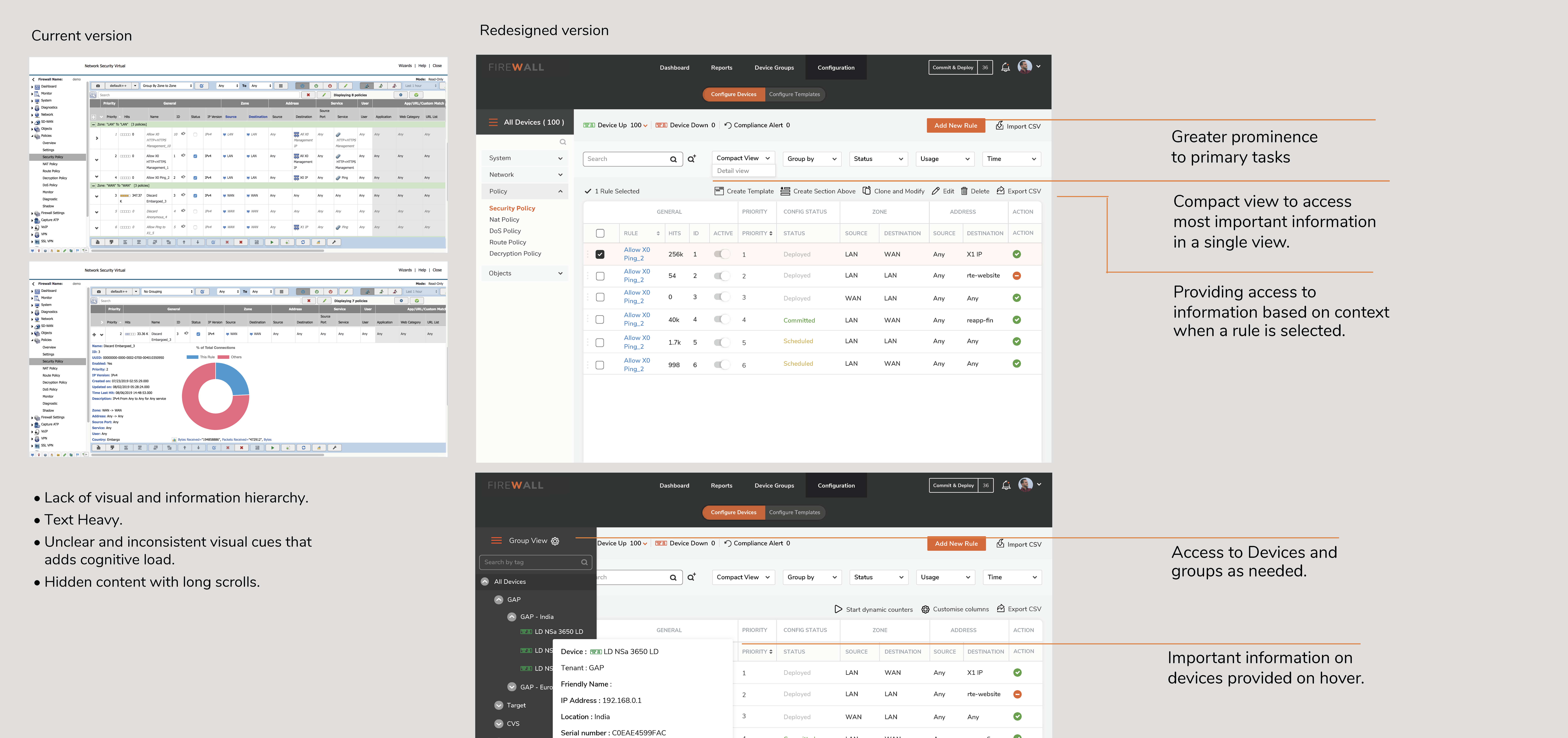
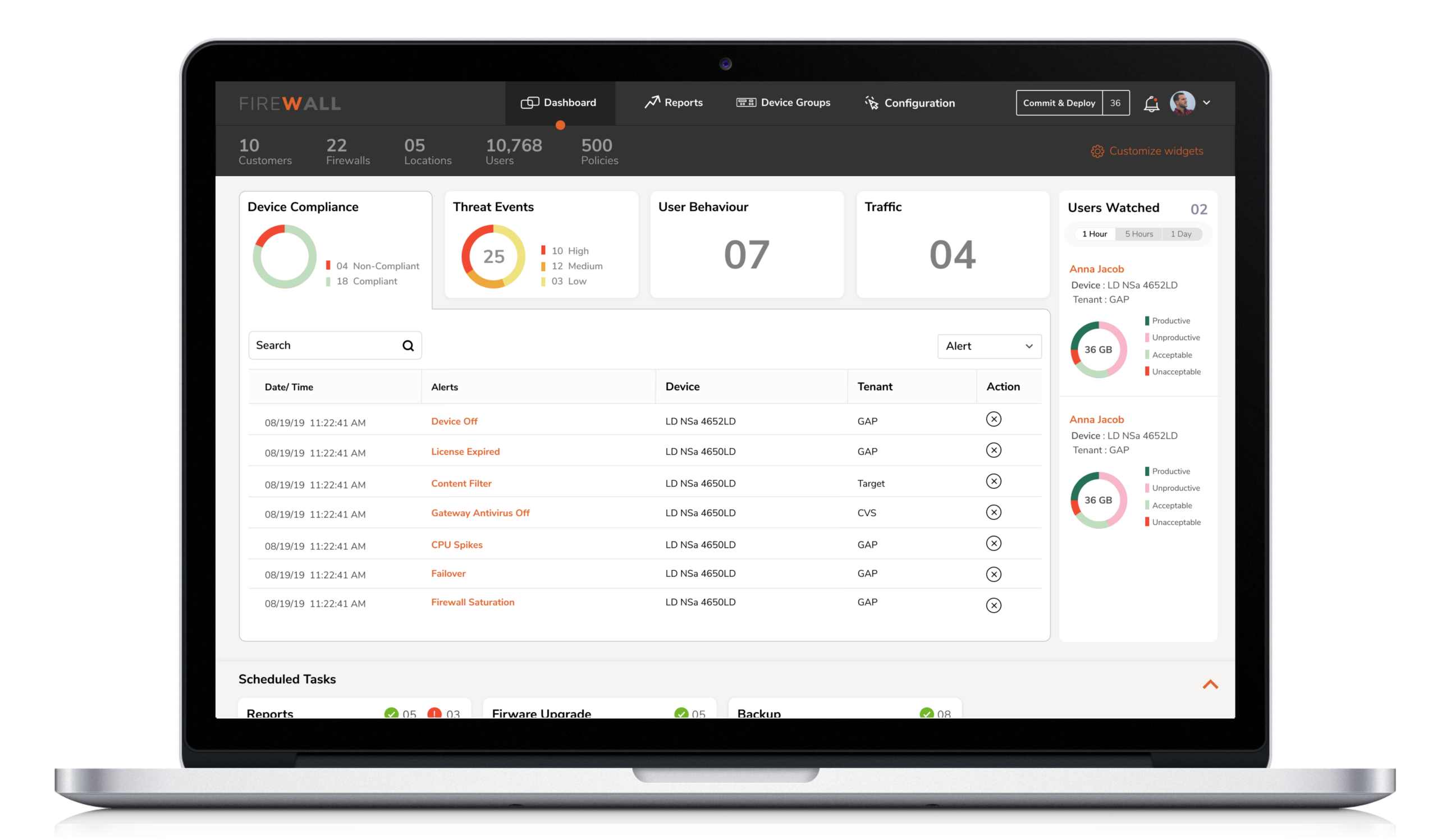
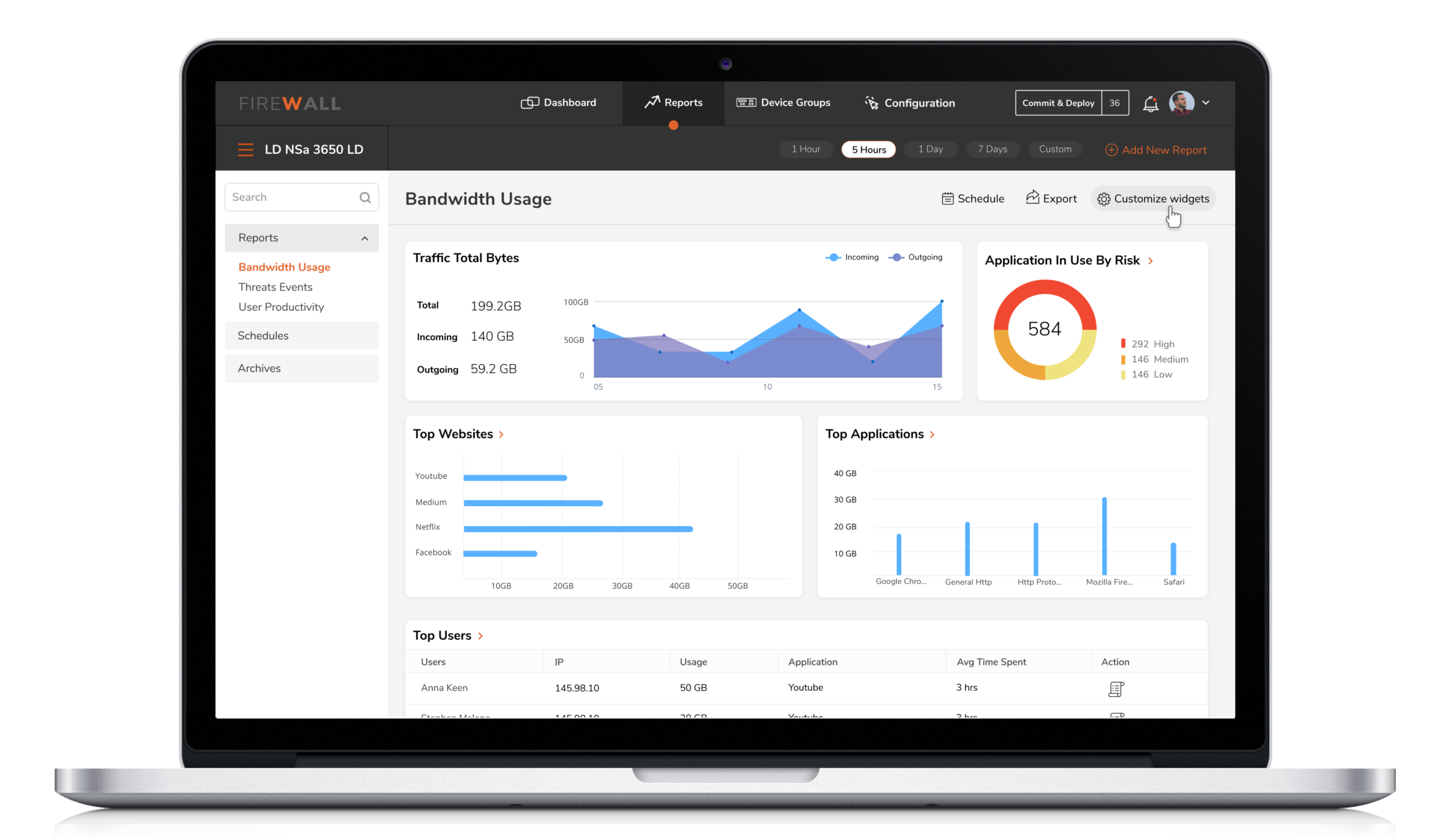
1. Real-time monitoring
1. Real-time monitoring
While managing hundreds of firewalls/devices across multiple customers, Security Engineers found it frustrating and time-consuming to navigate through individual devices to access dashboard level information. The absence of an actionable dashboard refrained them from using the current product functionality.
Solution
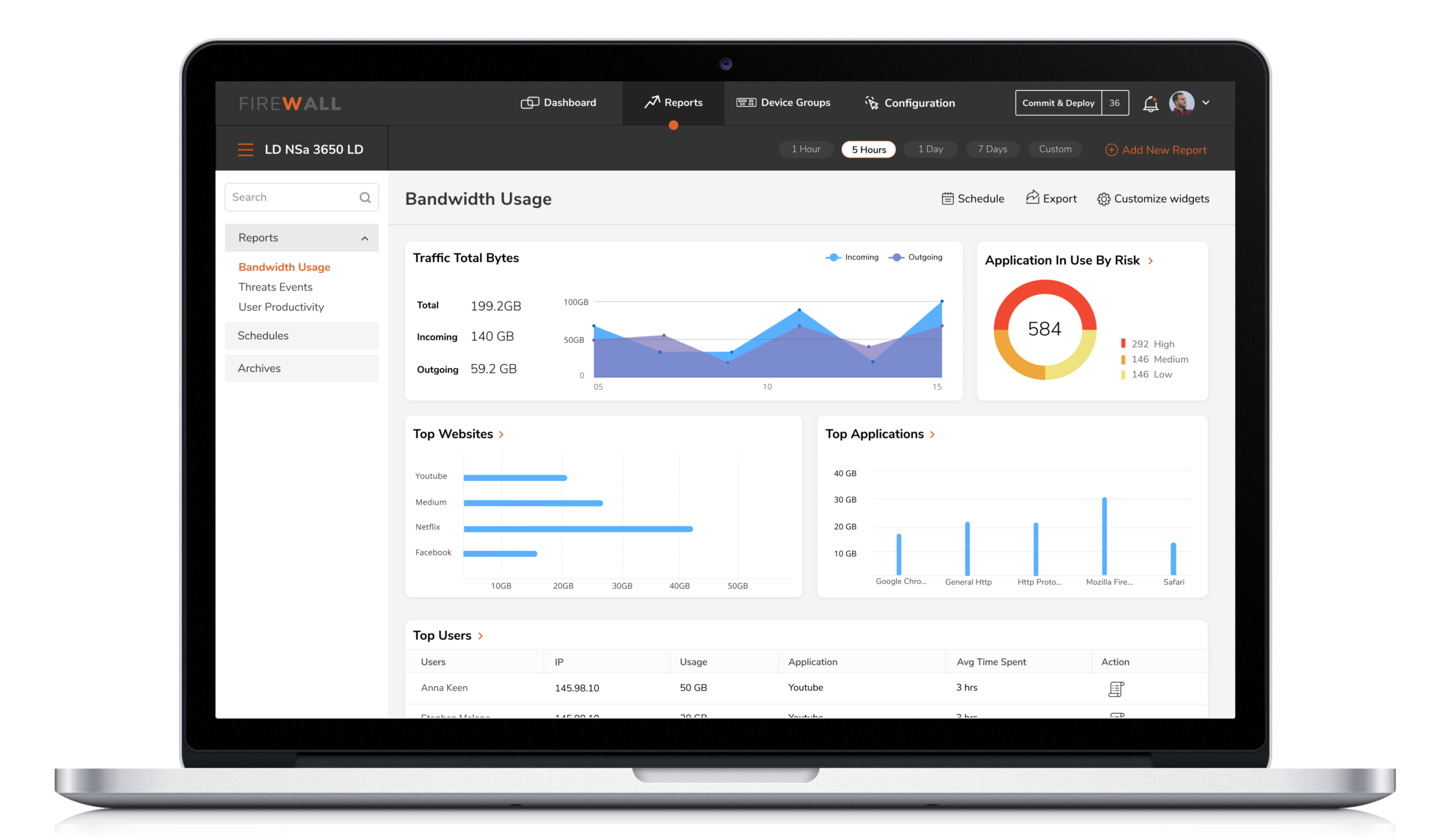
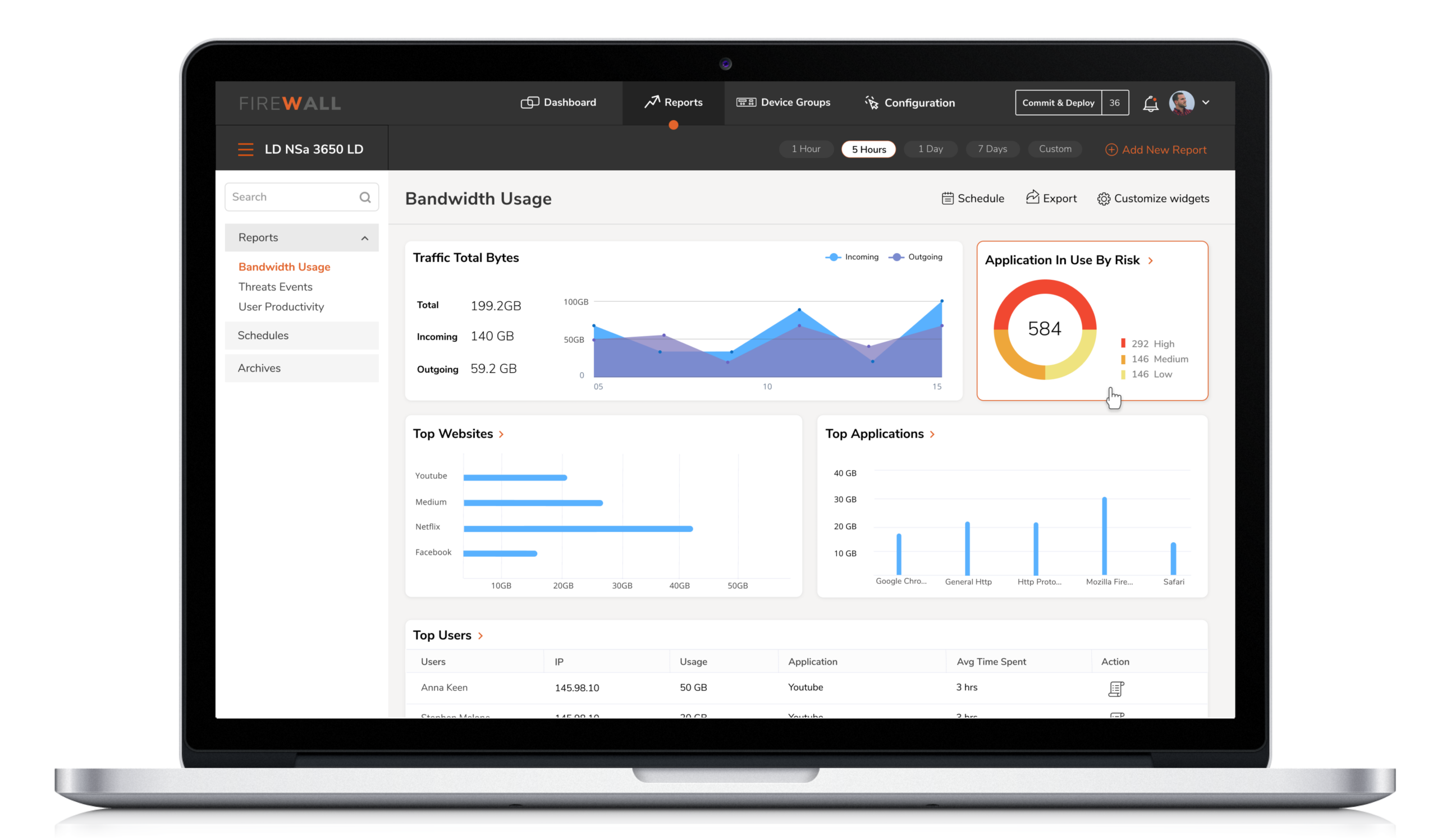
A one-stop-shop for real-time information ( of all devices ) based on criticality and relevance. The dashboard would provide actionable insights on anomalies, device compliance, and task schedule updates, to accelerate quick decision and immediate resolution.
While managing hundreds of firewalls/devices across multiple customers, Security Engineers found it frustrating and time-consuming to navigate through individual devices to access dashboard level information. The absence of an actionable dashboard refrained them from using the current product functionality.
Solution: A one-stop-shop for real-time information ( of all devices ) based on criticality and relevance. The dashboard would provide actionable insights on anomalies, device compliance, and task schedule updates, to accelerate quick decision and immediate resolution.
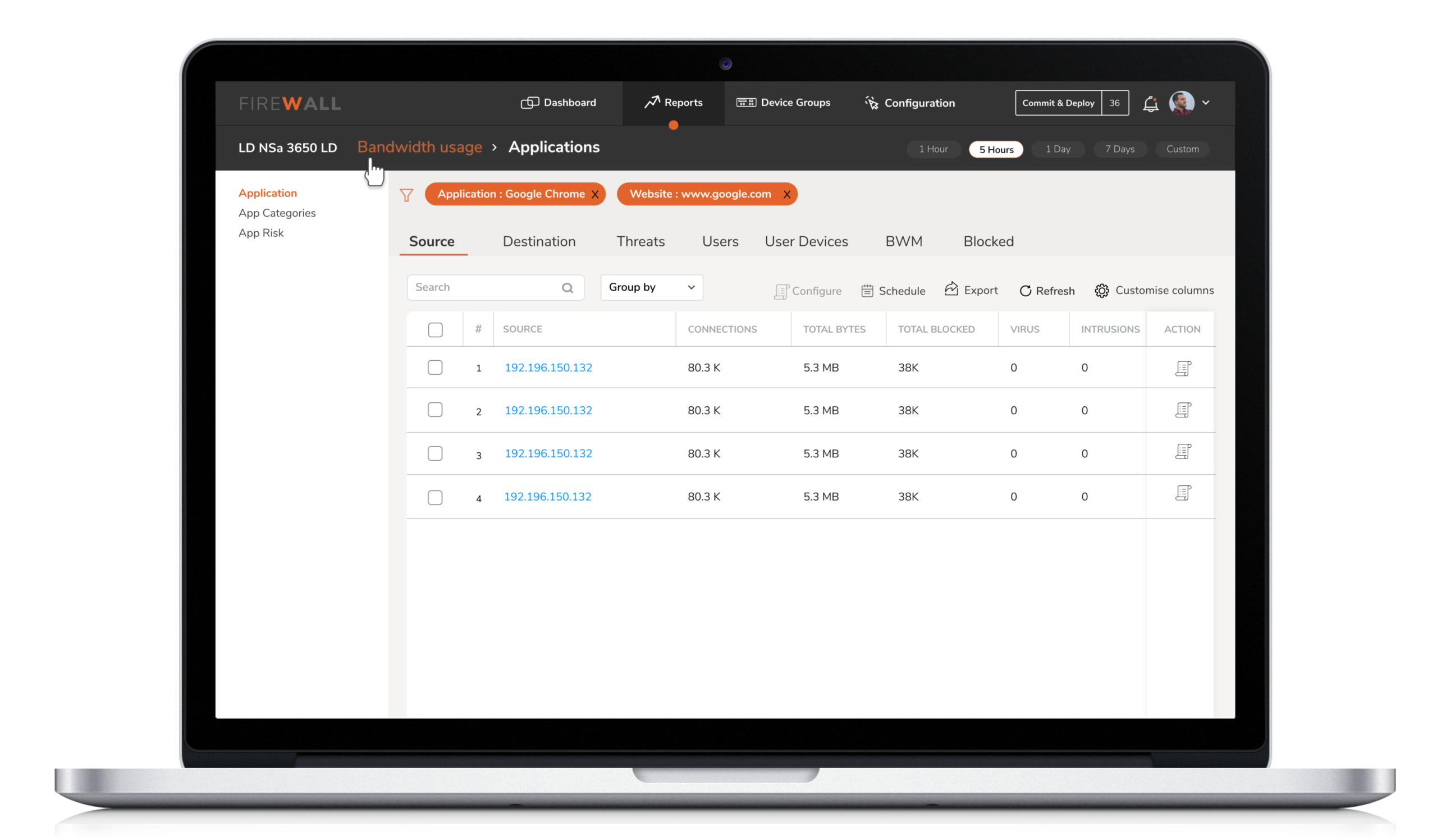
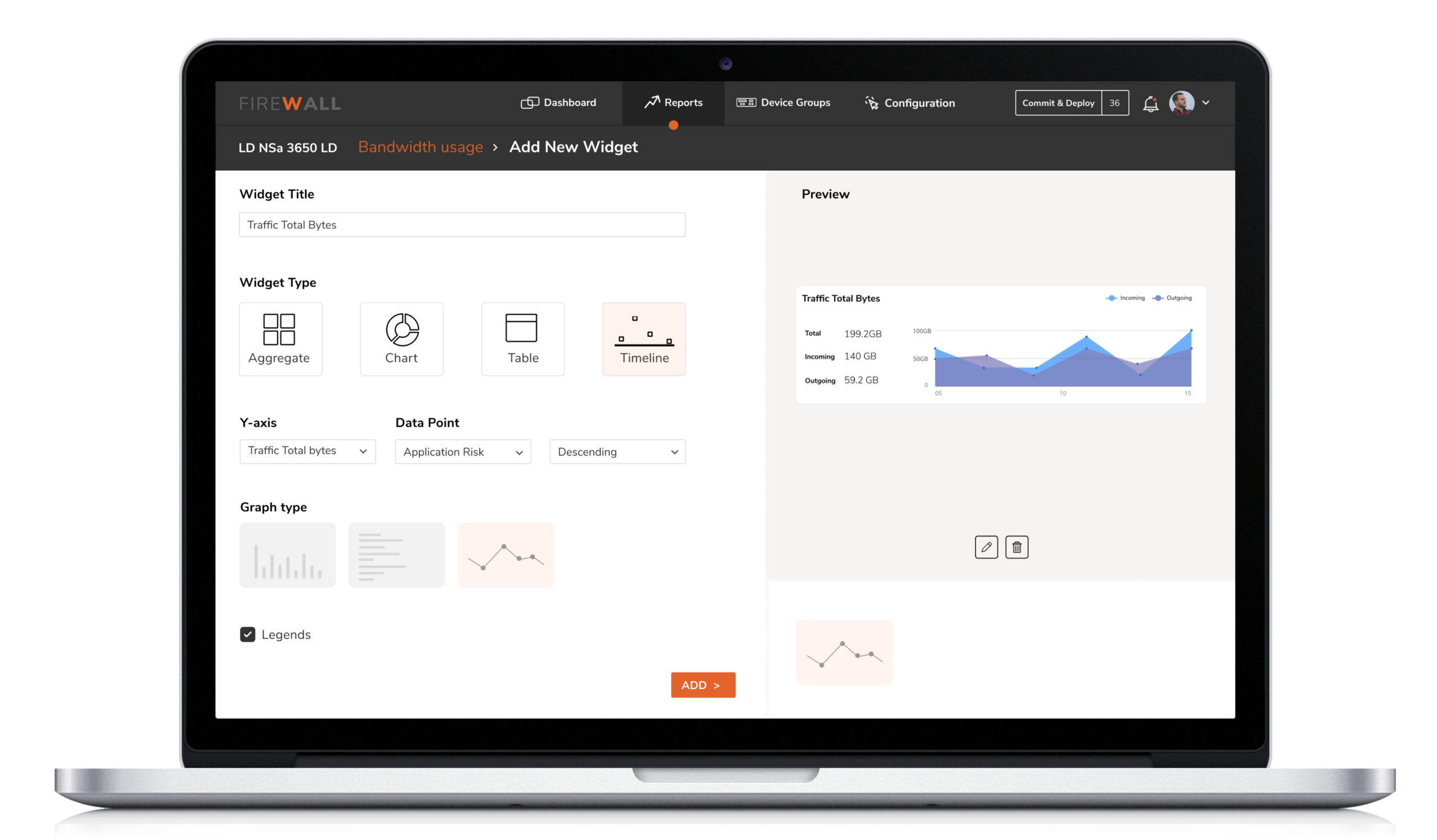
2. Customizable Reports
2. Customizable Reports
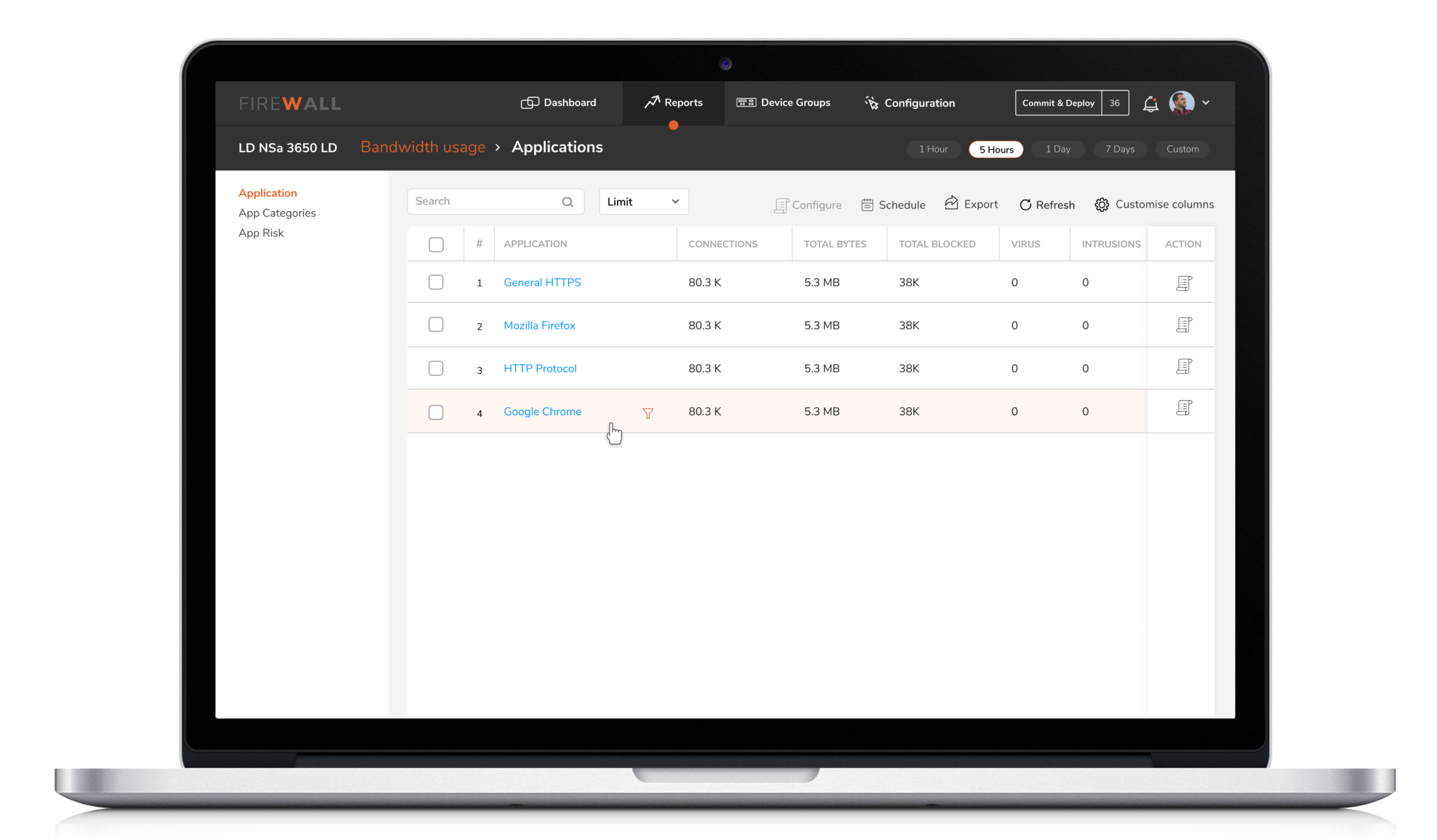
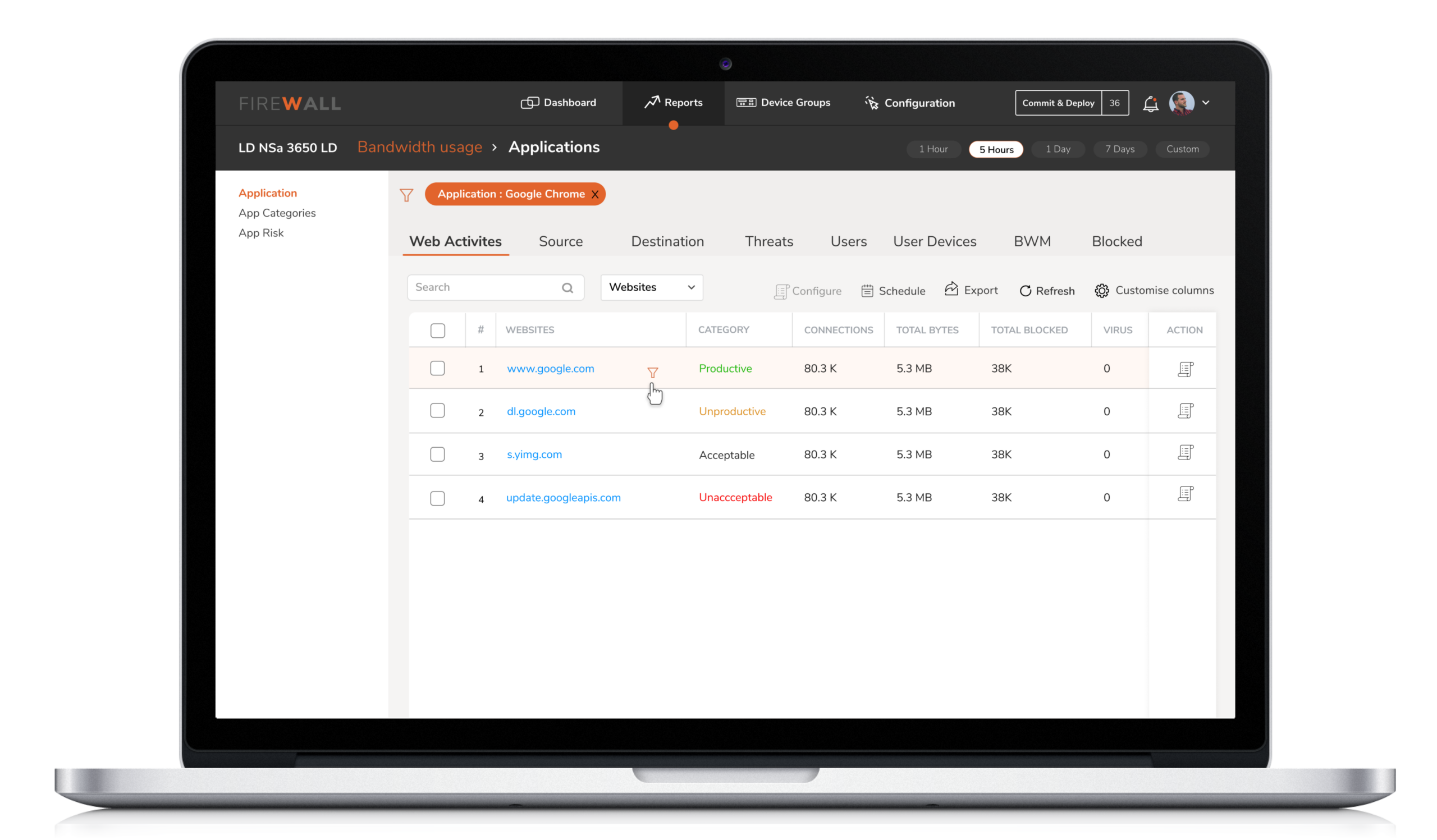
The inability of the tool to sieve information based on customer needs had led the Security Engineers to depend on third-party products like Grafana.
Solution
The reports provide an aggregate view of device performance over time, with the ability to drill down and diagnose through easy filtering. The engineers can view the reports at the device level or at the group level based on how they choose to group their devices.
While they are provided with visually refined reports, they have complete control over the customization of data and its visual representation ( i.e graph, table, chart ).
The inability of the tool to sieve information based on customer needs had led the Security Engineers to depend on third-party products like Grafana.
Solution : The reports provide an aggregate view of device performance over time, with the ability to drill down and diagnose through easy filtering. The engineers can view the reports at the device level or at the group level based on how they choose to group their devices.
While they are provided with visually refined reports, they have complete control over the customization of data and its visual representation ( i.e graph, table, chart ).
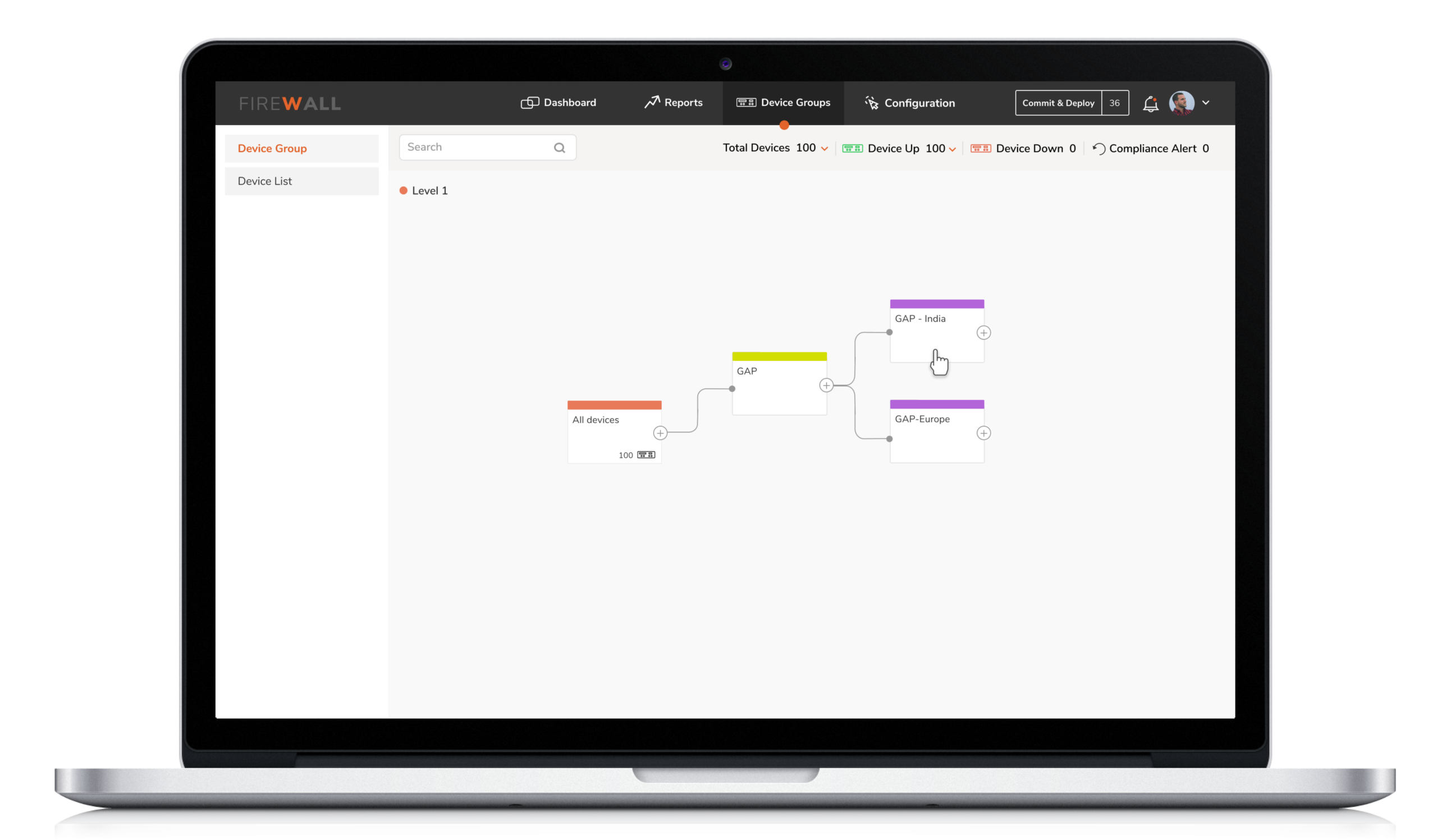
3. Personalized Device Grouping
3. Personalized Device Grouping
This feature allows the engineers to group devices/firewalls as per their organizational preferences, bringing flexibility and making it easy to push policies at the group level. This simplifies firewall management globally, making the task highly efficient.
This feature allows the engineers to group devices as per their organizational preferences, bringing flexibility and making it easy to push policies at the group level. This simplifies firewall management globally, making the task highly efficient.





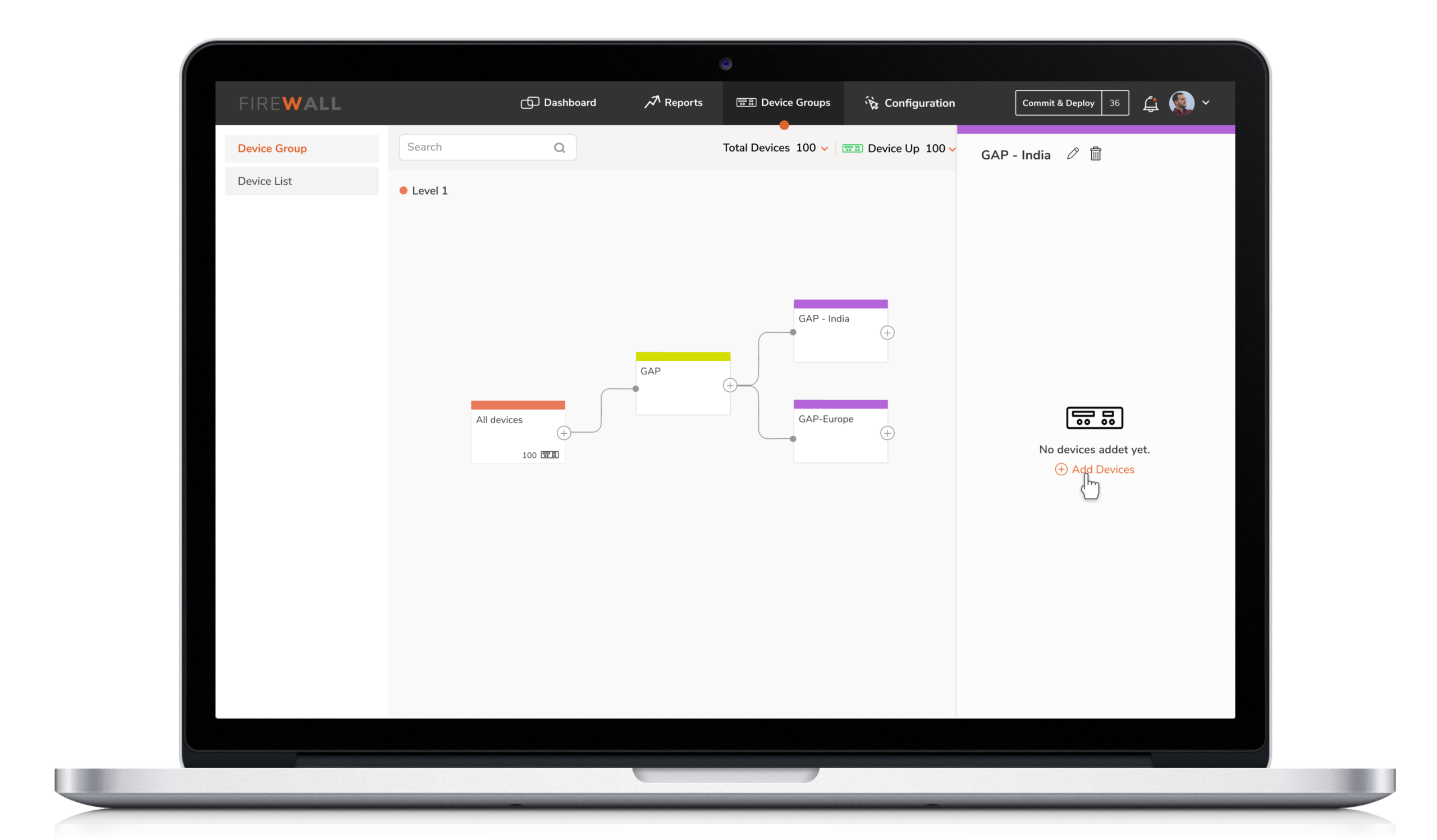
3. Reusable Templates
4. Reusable Templates
Security Engineers have the flexibility to either directly configure a device ( individual or group ) or save the configuration as a template based on the usage and requirement of the policy. A configuration template can have multiple types of policies which can then be pushed to groups or individual device.
Security Engineers have the flexibility to either directly configure a device ( individual or group ) or save the configuration as a template based on the usage and requirement of the policy. A configuration template can have multiple types of policies which can then be pushed to groups or individual device.
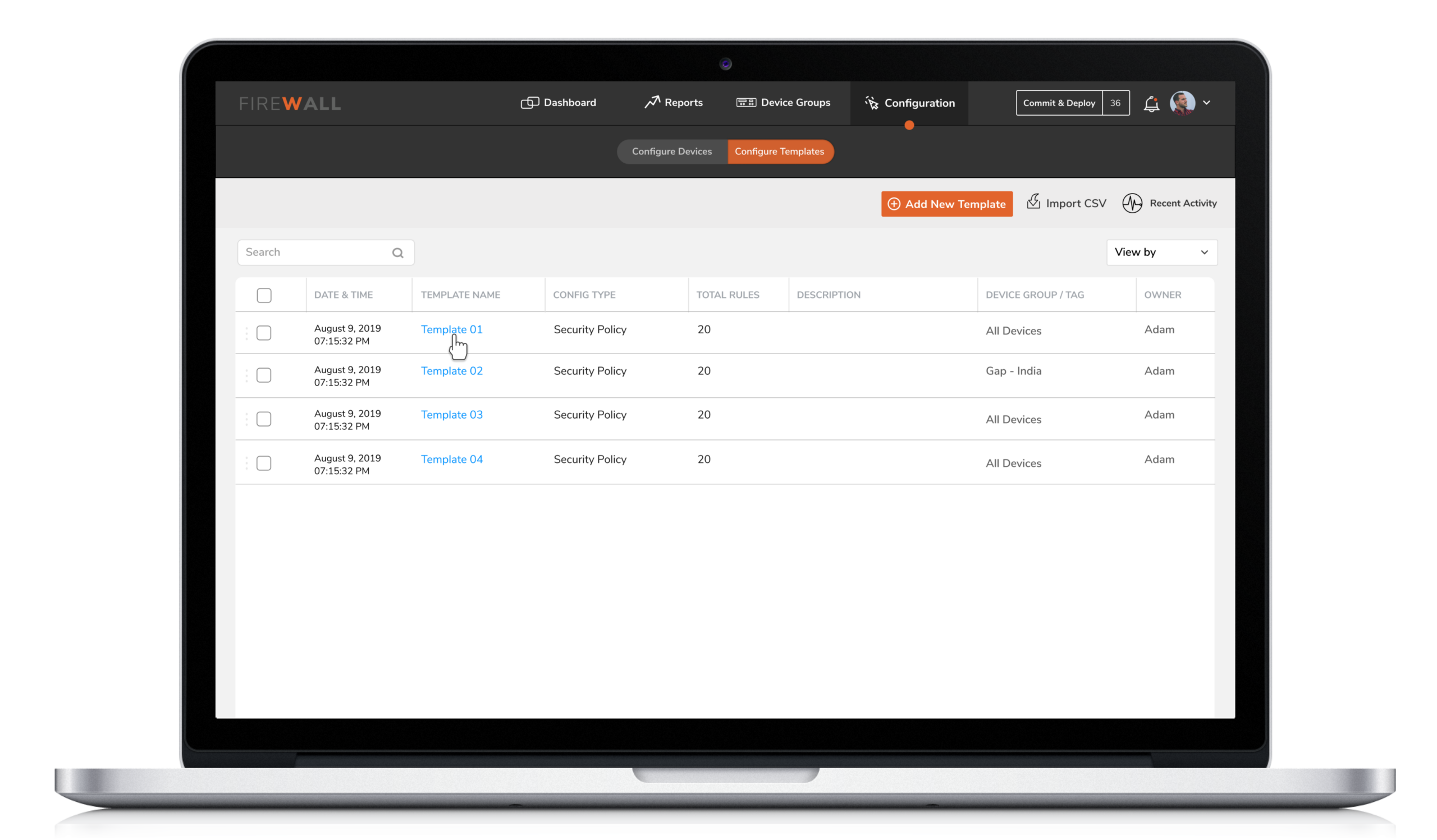
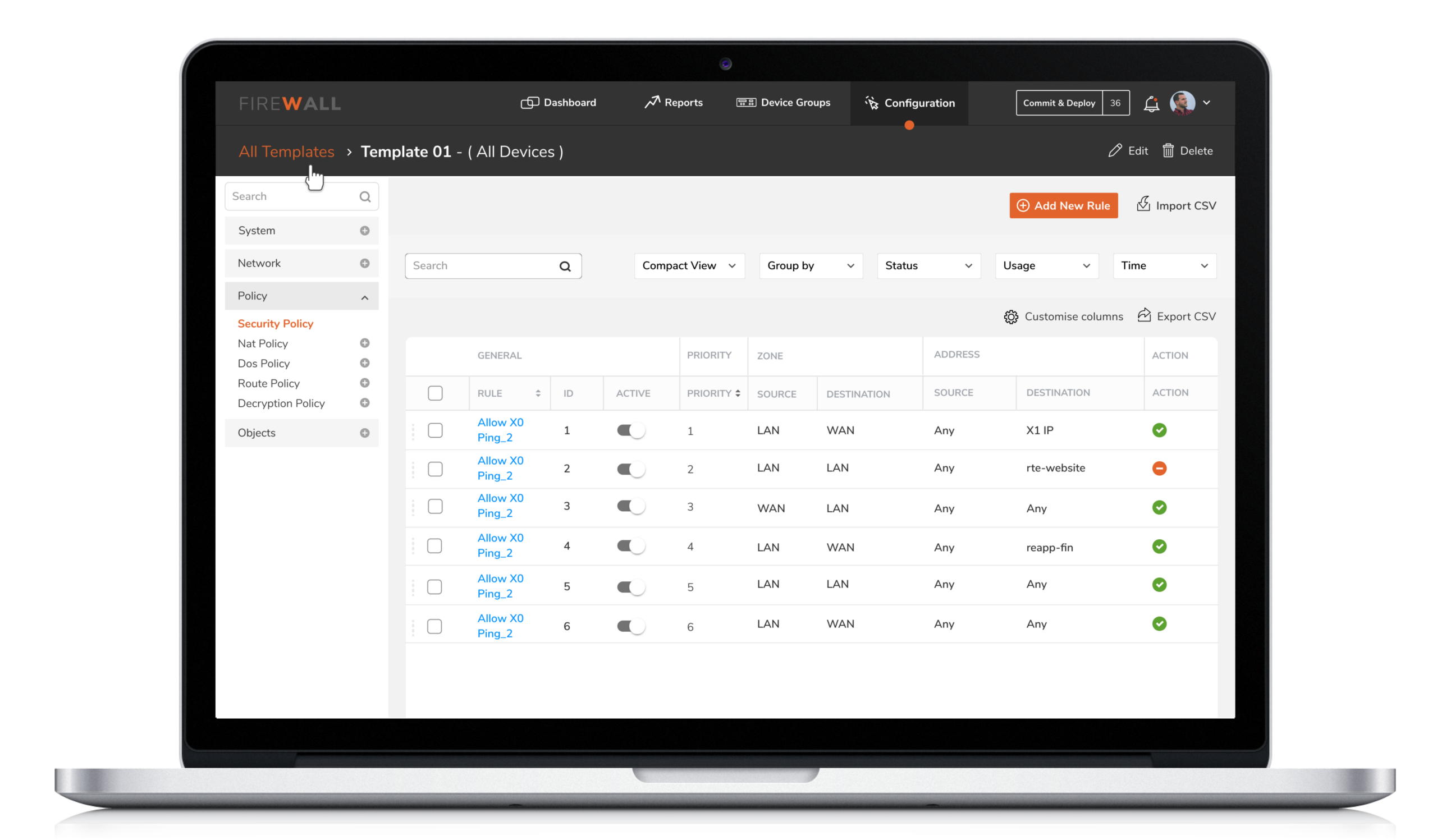
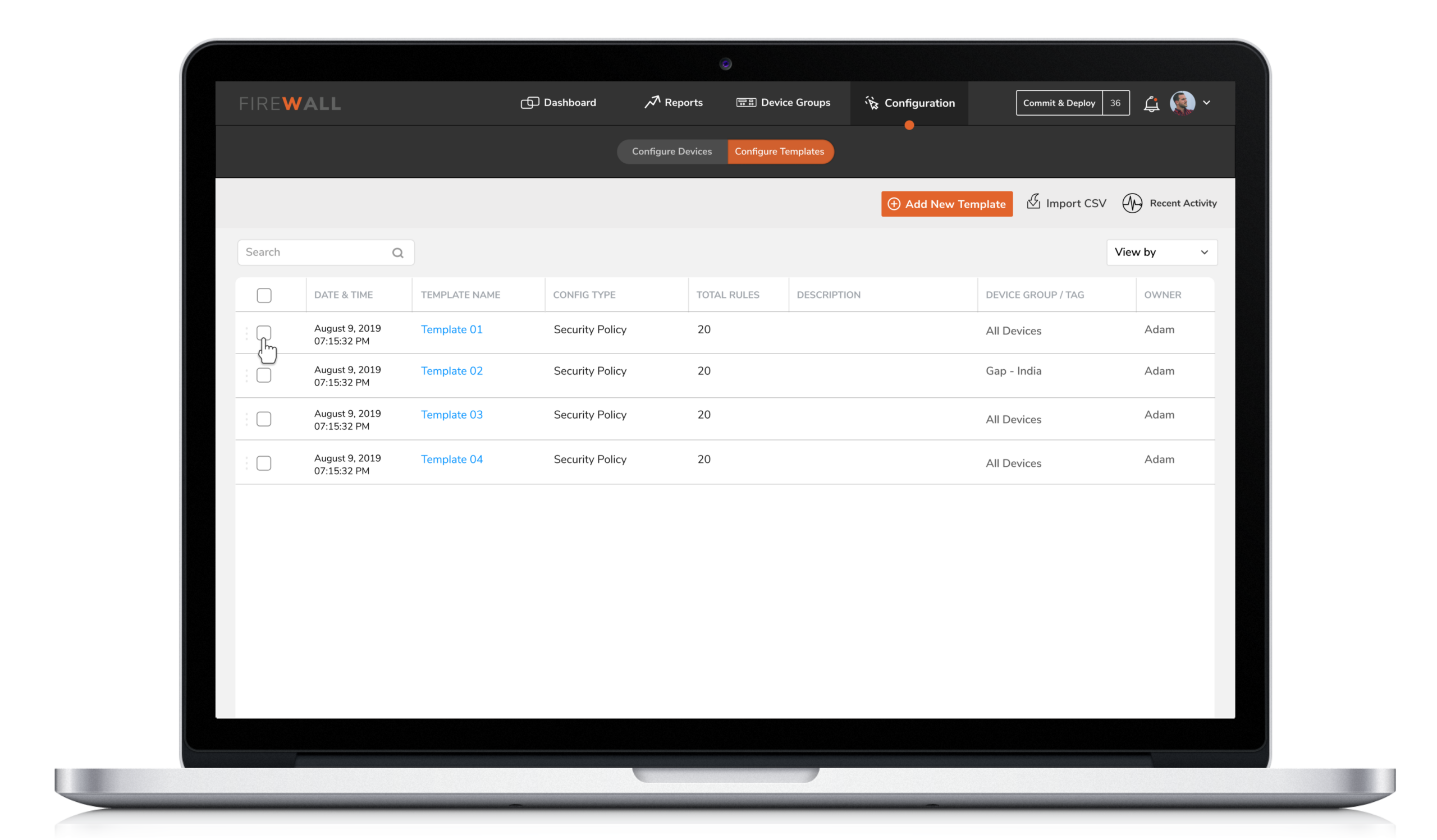
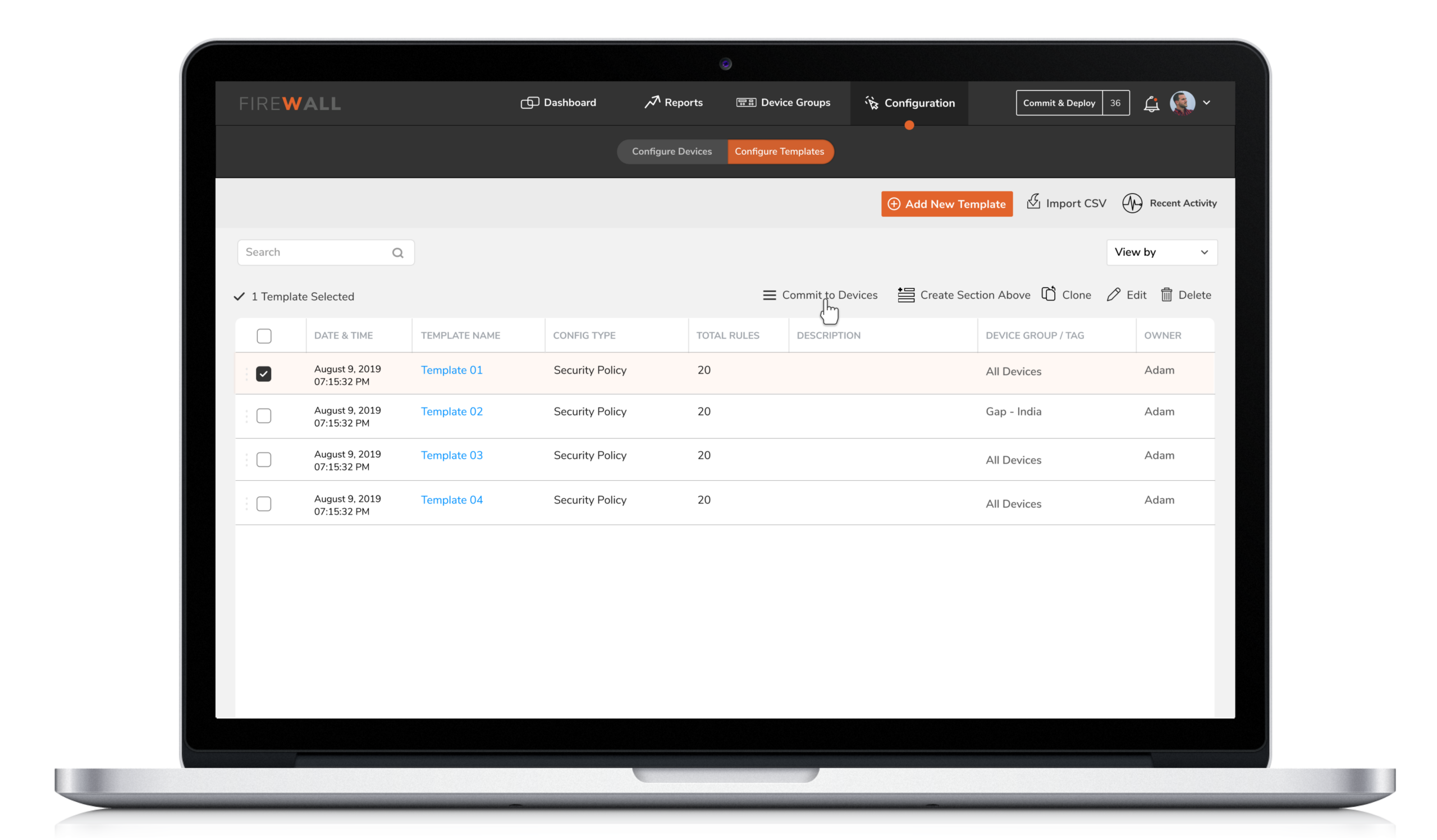
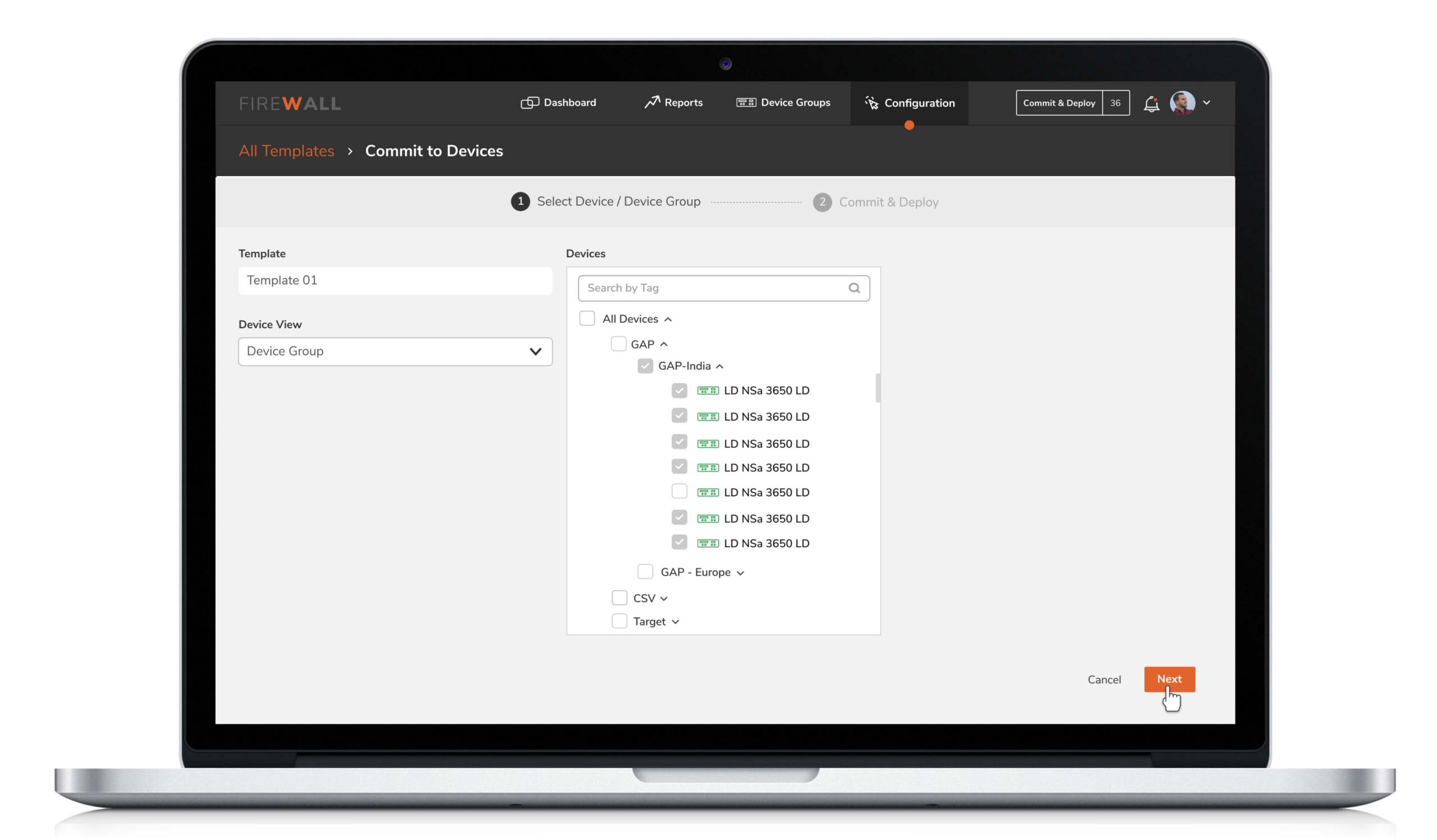
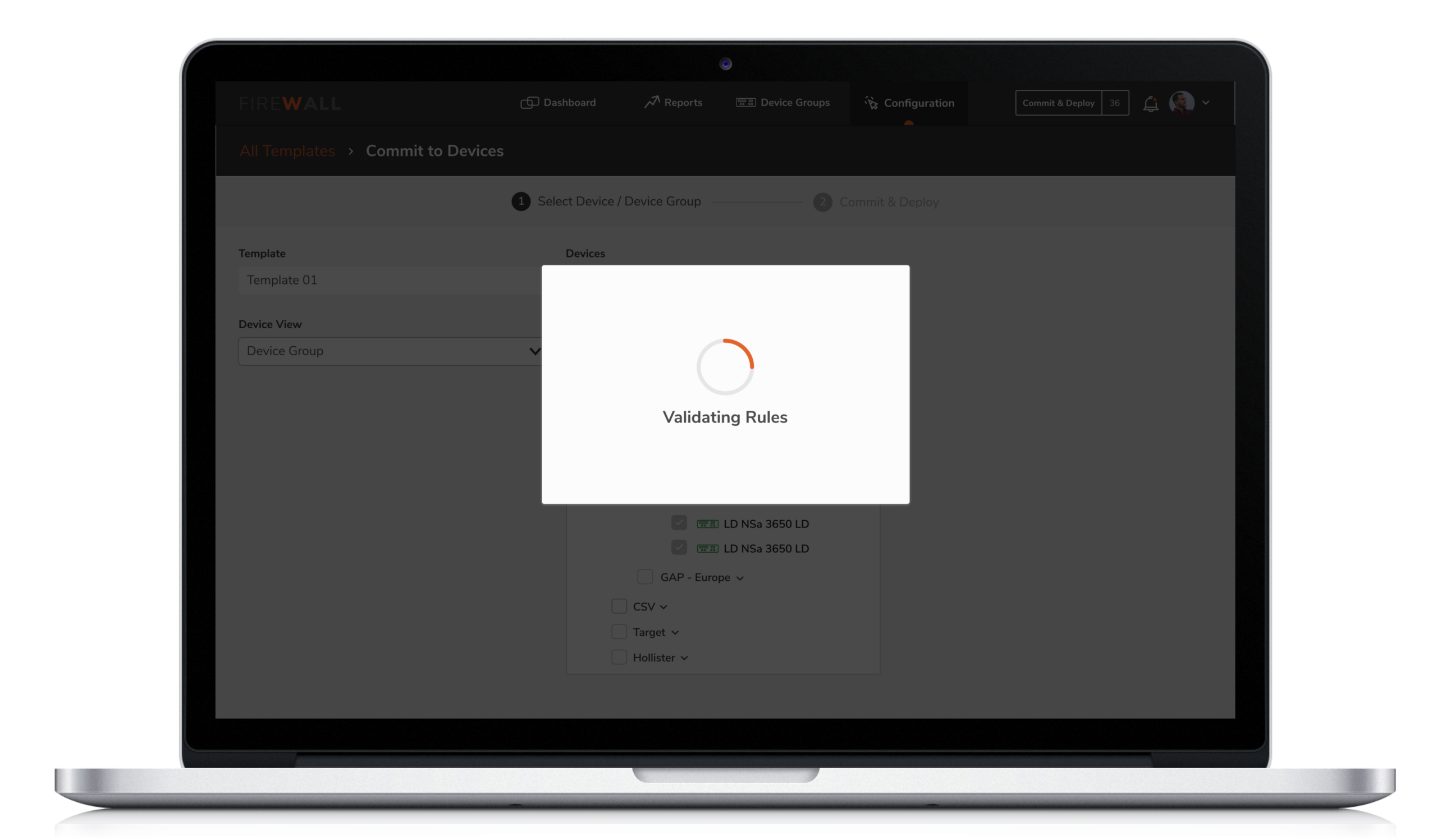
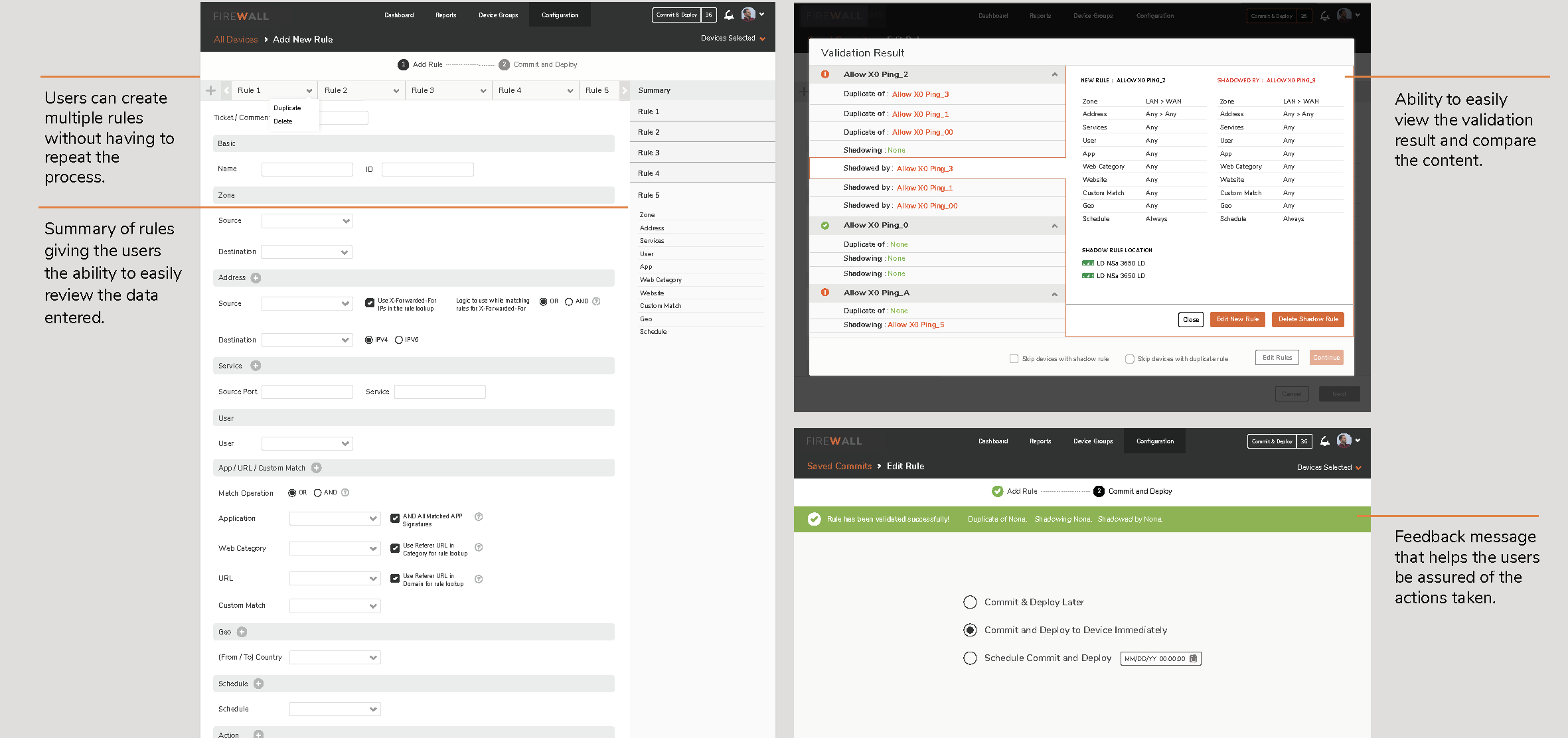
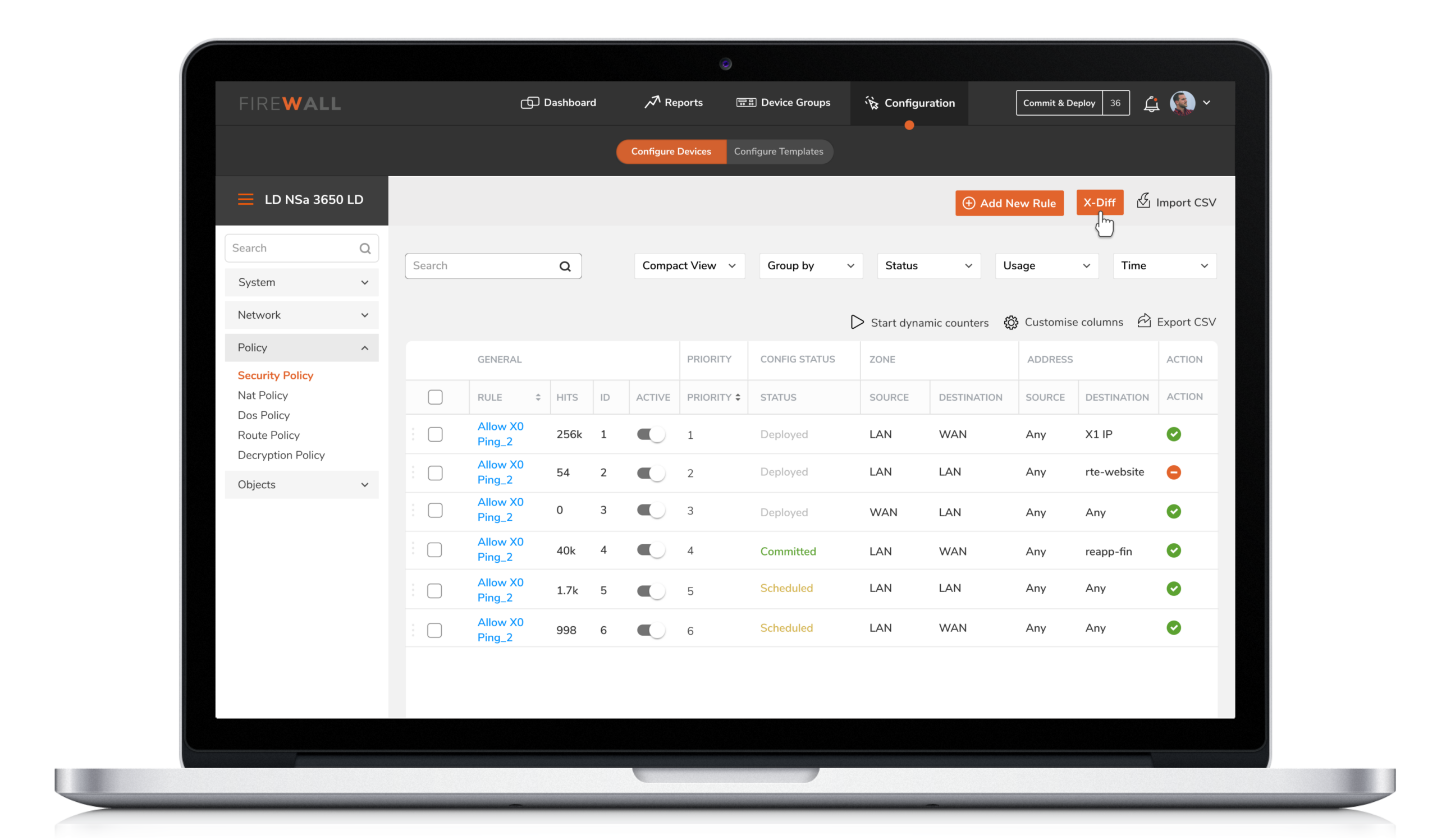
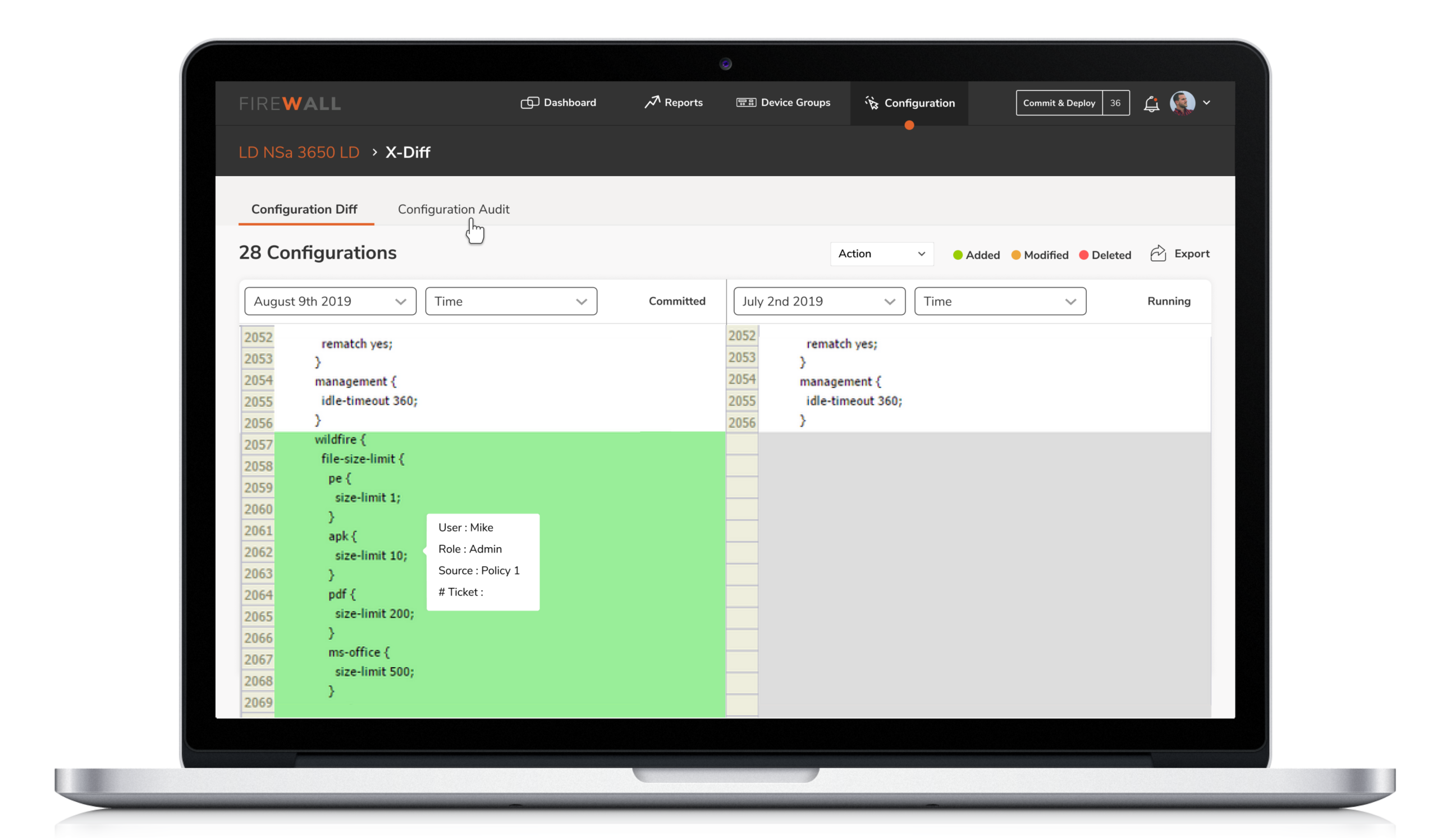
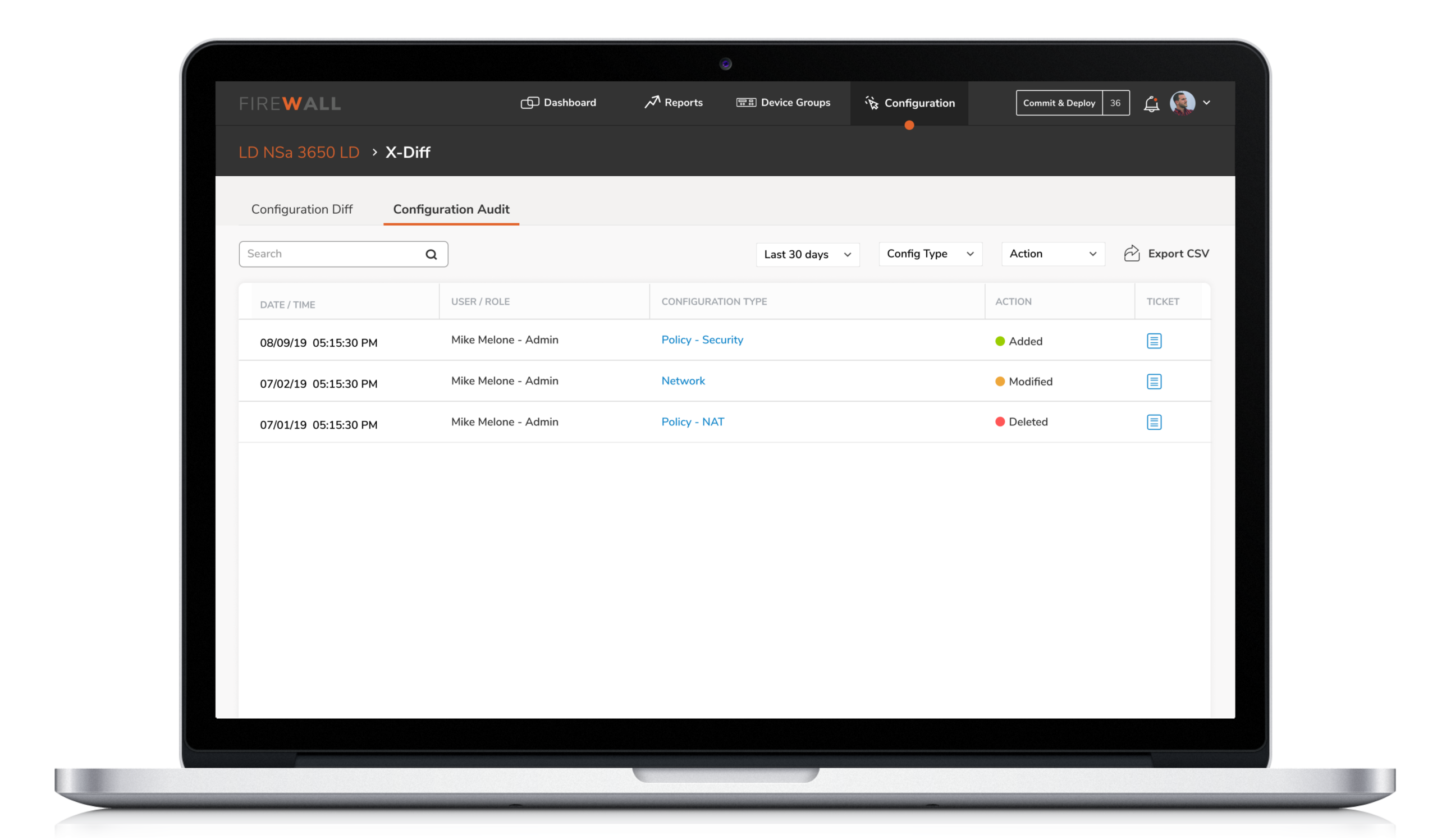
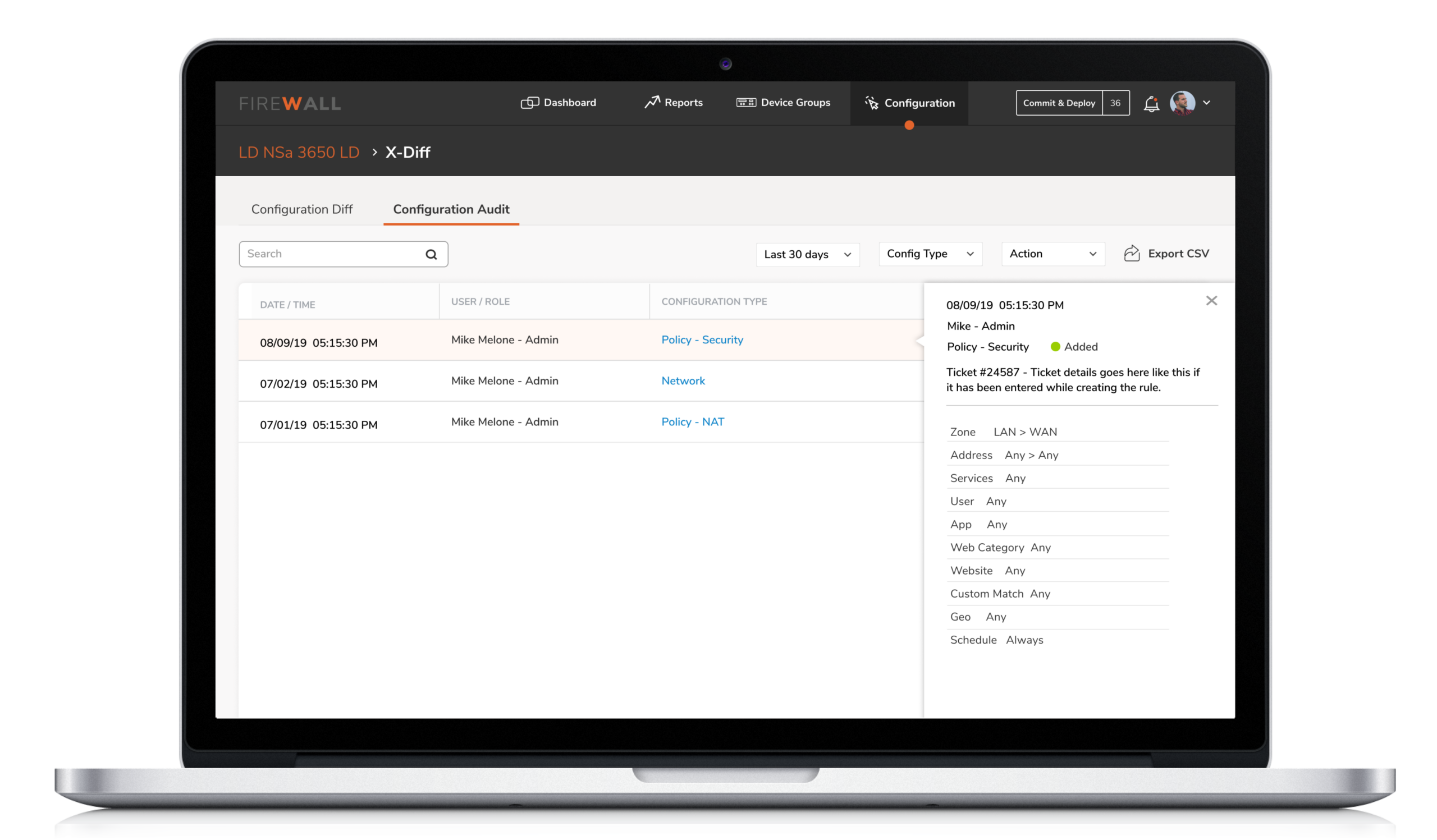
4. Configuration by X-Diff
5. Configuration by X-Diff
Users were unable to instantly track changes made on firewalls. This made it difficult for them to identify who initiated the changes. X-diff functionality helps compare and quickly examine two different versions of configurations with the ability to easily identify who made the changes, when and what changes were made.
Compare and quickly examine two different versions of configurations with the ability to easily identify who made the change, when and what changes were made.
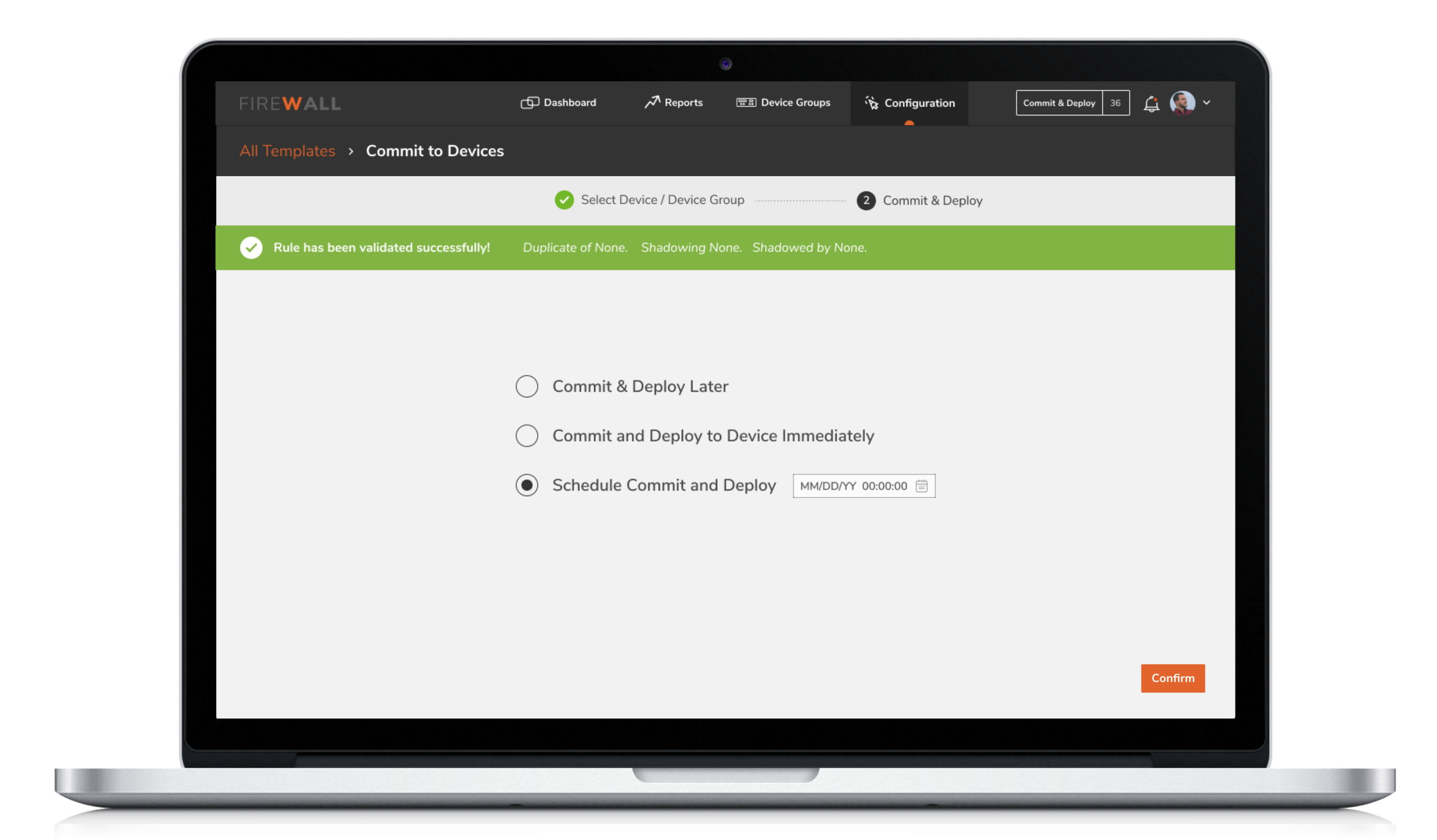
5. Revise and deploy
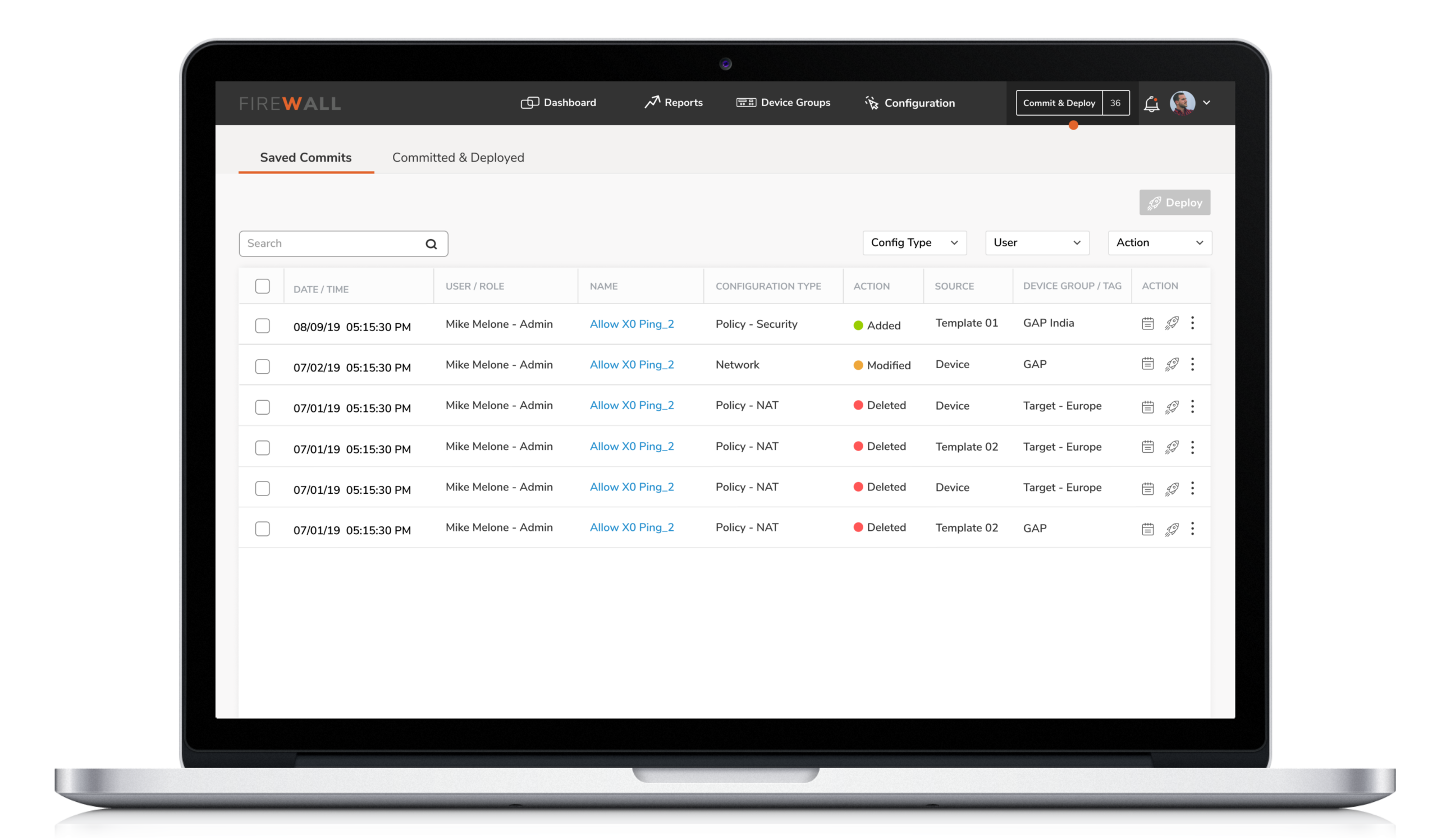
6. Revise and deploy
The functionality lets the Security Engineers save configuration changes and deploy them at a later time. This provides the flexibility to review the changes made by them or their team before it is applied to the devices. Furthermore, this ensures a safe step towards errors of omission or commission while configuring multiple devices.
The functionality lets the Engineers save configuration changes and deploy them at a later time. This provides the flexibility to review the changes made by them or their team before it is applied to the devices. Furthermore, this ensures a safe step towards errors of omission or commission while configuring multiple devices.
Design Evaluation
Design Evaluation
----------------------
----------------------
The prototype was tested with 12 users and evaluated based on a set of satisfaction parameters. We were able to gather 90% positive feedback with the rest 10% being minor iterations. Users remarked the new design cleaner, easy to follow and more productive, compared to the current one.
The prototype was tested with 12 users and evaluated based on a set of satisfaction parameters. We were able to gather 90% positive feedback with the rest 10% being minor iterations. Users remarked the new design cleaner, easy to follow and more productive, compared to the current one.
The designs were tested with 12 users and evaluated based on a set of satisfaction parameters :
The designs were tested with 12 users and evaluated based on a set of satisfaction parameters:
- I find the new design easy to use.
- I find the new design easy to navigate.
- I find the design’s functions are well integrated with each other.
- I feel confident using this design.
- I feel most people (team members, reporters) would learn this quickly.
- I find the new design easy to use.
- I find the new design easy to navigate.
- I find the design’s functions are well integrated with each other.
- I feel confident using this design.
- I feel most people (team members, reporters) would learn this really quickly.
User ratings :
User ratings :

Other key positive reactions received while the designs were shared with the users.
Key positive sentiments :
teenajose19@gmail.com / +91 62824 12702
